Webmasters using an ancient version of a WordPress plugin are putting site visitors ar risk because of an expired domain that exists in the source code of older versions of this plugin.
The issue was found by Sucuri on a website that was using the Flexytalk Widget WordPress plugin, renamed 16 months ago to FrescoChat Live Chat.
Because the owners of this plugin decided to rebrand their service as FrescoChat, they allowed two domains, flexytalk.net and flexytalk.com, to expire, replacing them with a new one, frescochat.com, as of version 3.1.8.
Malicious domain resellers pick up the expired domain names
These two domains were quickly picked up by two different entities that specialize in reselling domain names and were immediately parked.
Both operators decided that, while waiting for someone to buy their new domains, it would be a good idea to hijack all HTTP requests pointing to those two servers.
The authors of the Flexytalk Widget plugin had used these two domains to load content inside the WordPress plugin, leaving two dormant links to those two domains in all the WordPress sites that were still using the older plugin versions.
Domain resellers decided to push ads, scareware
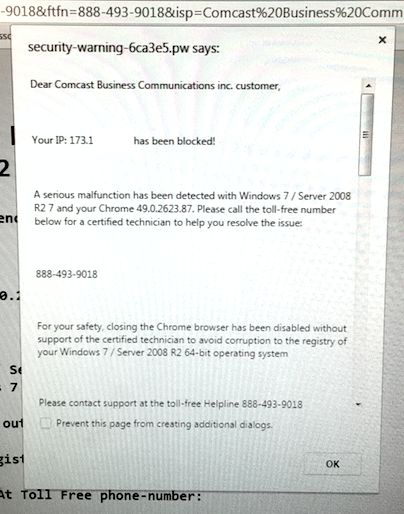
The operator of the flexytalk.net decided to deliver popup ads, some of which were downright malicious browser-locking scareware that tried to fool users into calling a tech support number.
The owner of the flexytalk.com domain did the same but only delivered popup ads, with no scareware. Additionally, the plugin was also hardwired to collect the username and password for the FlexyTalk service and send it via HTTP to the flexytalk.com domain.
The domain owner could have easily collected all those credentials and used them to hijack the user's current FrescoChat accounts or other accounts on which the owner might have reused the username and password. There is no evidence that the domain reseller collected this data.
The bad news is that these two domain resellers that registered the two expired Flexytalk domains also registered over 100,000 other parked domains, on which they are probably employing the same ad-pushing tactics.
Webmasters are to blame, not plugin developers
Sucuri's Krasimir Konov points out another problem, putting the actual blame on WordPress website owners who forgot to do one basic thing: UPDATE!
"Three versions with the new [FrescoChat] domain names have been released since then [16 months ago], but still some webmasters refused to update the plugin, which is really strange, because it’s a live chat widget and no one needs a live chat that doesn’t work (and it didn’t work since they changed their servers 16 months ago)."
This comes to show once again that, in most website compromises, the lack of timely updates is the main source of problems.
Three weeks ago, Sucuri discovered a similar incident, when a Chinese domain reseller bought the expired domain name used by a popular WordPress theme developer and used it to push ads to all websites that employed that theme.

 14 DAY TRIAL //
14 DAY TRIAL //