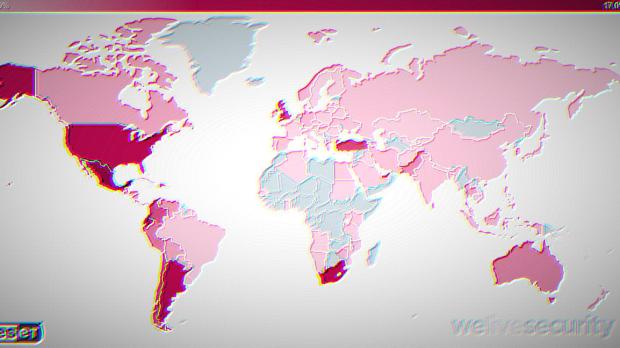
A new ample spam campaign is spreading the Emotet banking Trojan to unsuspecting victims via maliciously crafted emails as discovered by ESET Research in November.
Emotet, infamous for being a modular banking trojan, recently got updated with a new email exfiltration module for harvesting email messages from infected systems, as observed by Kryptos Logi's security researchers.
The Emotet malware can also steal proprietary info, login credentials, and Personally Identifiable Information (PII), which is the leading cause behind identity theft incidents.
Moreover, Emotet is also known as being used as a dropper or downloader for other possibly more-harmful subsequent malware payloads.
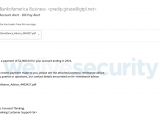
As reported by ESET Research, this November's Emotet-powered spam campaign is spreading the malware using emails that contain malicious attachments posing as either invoices, bank account alerts, or payment notifications, or hyperlinks to domains controlled by the bad actors behind the Trojan as an alternative infection starting point.
The target compromise process will automatically begin when the victims open the malicious attachments and, once the victim activates the infection mechanism (Word macros or PDF links), the Emotet payload is downloaded, installed, and launched on the system.
The Emotet malware spread by this spam campaign also drops the Trickbot and IcedID trojans
Subsequently, the malware reports the successful infection to its command-and-control (C&C) server which sends back detailed instructions on what are the modules and payloads it needs to download.
Depending on the extra modules it installs on the victim's machine, Emotet will next be able to perform a wide range of tasks from self-propagation through the network and harvesting sensitive info to port forwarding.
Emotet's secondary payloads are the IcedID banking Trojan that bundles advanced browser manipulation tactics and Trickbot, a highly-customizable and modular information-stealing botnet agent which uses compromised IP cameras and routers as its C&C servers.
Because of the threat actors behind Emotet being able to deploy new modules to the botnet at any given time using the C&C servers, even machines infected with older versions of the malware are not safe.
This is especially true given that the Emotet masters are known to slowing down the botnet's activity and using it in large-scale spam campaigns just like the one recently detected by ESET Research.
 14 DAY TRIAL //
14 DAY TRIAL //