DarkSide, the group responsible for the notorious ransomware attack used in the attack on Colonial Pipeline, generated national panic and skyrocketing gas prices. While they announced a retirement, their platforms are still operational.
By May 23, the DarkSide cybercriminal group agreed to provide decryptors for all ransomware targets and pay for outstanding financial obligations. While the news of the group's surrender is heartening, the threat posed by the bad actors that use its ransomware has not been eliminated.
According to RiskIQ, researchers discovered that some of the infrastructure associated with UNC2465, which the group used to deploy malware other than the DarkSide ransomware, is still operational and could pose a threat.
RiskIQ Discovers DarkSide Affiliate Infrastructure
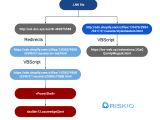
According to FireEye, an affiliate used phishing emails and legitimate services to deliver SMOKEDHAM, a PowerShell-based.NET backdoor. An LNK file reported by FireEye and another discovered by RiskIQ through their own Internet Intelligence Graph, both linked to the same two URLs that executed a PowerShell script linked to two URLs. One of these, a Shopify connection, was mentioned by FireEye but not the other. DarkSide affiliates' use of the Shopify platform has not been published in open source.
Shopify is an e-commerce platform for online retailers and retail point-of-sale systems that has reportedly been used in hundreds of campaigns by cyber actors.
The RiskIQ Shopify link pointed to another URL embedded within some VBScript on the website, that FireEye claimed the affiliate used as an EMPIRE C2. RiskIQ discovered a redirection on this page to a second Shopify link, that in turn linked to a third.
The file hosted on this third Shopify host contained PowerShell code, that was the SMOKEDHAM.NET backdoor mentioned by FireEye. RiskIQs’s review of this code revealed the ability to perform keylogging, take screenshots, and execute arbitrary.NET commands, all of which are consistent with FireEye's definition of SMOKEDHAM.
The data obtained by UNC2465 is submitted to a server as the User-Agent using the victim's current platform identifier and version amount. This host takes advantage of Microsoft Azure cloud hosting. Although the hosts found by the researchers are no longer active, the malicious files, as well as the C2, are still active as of May 17.
UNC2628
According to FireEye, the group UNC2628 has formed alliances with other RaaS providers such as Sodinokibi (aka REvil) and Netwalker. RiskIQ discovered a malware sample associated with lagrom.com while reviewing the BEACON C2s issued by FireEye. This sample was Sodinokibi ransomware delivered via Cobalt Strike, according to VirusTotal detections.
Defend Against DarkSide Affiliates
Even though DarkSide RaaS is no longer operating, some of the supporting infrastructures are still operational and can serve malware though the known precursors to those live sites are not currently active in most instances.

 14 DAY TRIAL //
14 DAY TRIAL //