Iranian hackers believed to be part of infamous group Charming Kitten are using a new phishing technique to target high-profile victims across the world.
Security company Certfa Lab warns that the cybercriminals now pose as well-known journalists in an attempt to trick specific public figures into entering their usernames and passwords on crafted websites.
The hacking group is specifically focused on stealing email information and extracting contact details, and this new fake interview scheme aligns with previous efforts in this regard.
In the latest attack, Charming Kitten hackers used the identity of former Wall Street Journal and currently New York Times journalist Farnaz Fassihi to send fake interview requests to potential victims.
“This interview could motivate the youth of our beloved country to discover their talents and move toward success. Needless to say, this interview is a great honor for me personally, and I urge you to accept my invitation for the interview,” the email reads.
The message includes several links using the short URL format that points targets to pages where some information, including IP address, operating system, and browser data can be collected.
Malicious links
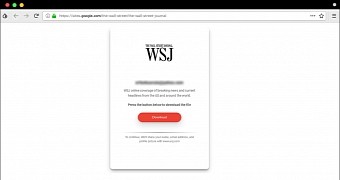
The attack, however, is conducted through an exclusive link that allegedly includes the interview questions and which points targets to a page hosted on Google Sites. A download button on this page redirects them to a second fake page requesting emails, passwords, and two-factor authentication codes.
The hackers also use malware with backdoor capabilities to deploy additional payloads and extract more information from a compromised device.
While it’s not yet known how many people fell victims to this type of attack, Certfa says the first VirusTotal scan was performed on October 3, 2019.
“This malware, which is identified as a Win32/Backdoor by antiviruses, is a mid-level piece of malware - due to lack of design sophistication - with various harmful capabilities. Our assessment shows the malware causes changes in the Windows’ Firewall and Registry settings in order to run automatically itself and gathers information from the victim’s device and sends it to its developer,” the analysis reads.
Users receiving emails are recommended to reach out to journalists directly and avoid downloading files attached to these messages.
 14 DAY TRIAL //
14 DAY TRIAL //