A trio of researchers from security firm Bishop Fox revealed last week a way to exploit Apple's OS X Messages app that allows attackers to steal a victim's chat history.
The vulnerability does not attack the app's encryption capabilities but relies on local software bugs and a little bit of social engineering, requiring victims only to click on a link supplied by the malicious third-party.
But don't panic, according to the three security researchers, the bug was properly reported to Apple's staff, who already fixed it in their regular monthly security update last March.
This issue was revealed only last week to allow the majority of users to upgrade their apps. If you're using the latest versions of OS X and the Messages app, then you have nothing to fear about.
The bug was a classic XSS
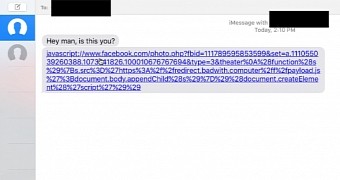
The three researchers that discovered this flaw are Shubham Shah, Joe DeMesy, and Matthew Bryant. They found out that by replacing the http:// protocol at the start of a link with javascript://, the link would execute locally inside the Messages client.
Since the Messages client is a glorified version of the WebKit rendering engine used for displaying content in Safari and all the Chromium-based desktop and mobile browsers, classic XSS (cross-site scripting attacks) could be used.
The three crafted a malicious link that when clicked would jump from the user's current chat tab to other local tabs, and steal all the content found inside them, uploading it to the attacker's Web server. Furthermore, the exploit could also scour the local chat archive and exfiltrate all previous messages as well.
Attackers could also steal file attachments such as images
If file attachments such as photos are inside the chat or the archive, those will be stolen as well. If the user had SMS forwarding enabled, the attacker could also recover messages sent to and from the victim's iPhone.
"Web application security flaws are no longer limited to only the browser but rather have found their way into native applications too," the three researchers noted. "While it can be productive for developers to use web technologies such as WebKit, [...] web application security best practices must still be followed."
Back in March, security researchers found a way of decrypting images and videos sent in encrypted conversations on older iOS devices. Also last week, security researcher Jose Rodrigues found a flaw in Siri that allowed attackers access to a phone's photos and contacts list.
Below is a video showcasing how the bug works. Proof-of-concept code is also available on GitHub.
 14 DAY TRIAL //
14 DAY TRIAL // 