We’re only a few days away from the moment Apple is supposed to push the go-ahead button for the brand-new iOS 13, and here’s a security researcher coming up with an exploit that exposes contact information on an iPhone.
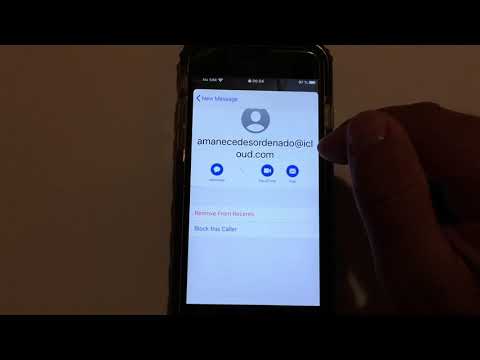
Jose Rodriguez says the lockscreen bypass makes it possible for anyone to trick an iPhone running iOS 13 to grant access to stored contacts, all using nothing more than a FaceTime call.
A successful hack requires physical access to the vulnerable iPhone, and the security researcher says that Siri’s voiceover support can be used during the FaceTime call to obtain access to the contact list.
However, no other data is exposed, like messages or photos, albeit access to contact information means an attacker could get data like emails, phone numbers, and other sensitive details.
Fix available in iOS 13.1
The researcher, who has previously discovered a similar lockscreen bug in iOS 12.1, says he already reported the problem to Apple back in July, but no fix has been issued whatsoever. He claims the same exploit still works in the iOS 13 Gold Master build, which is virtually the same as the final production build that Apple promised to ship on September 19.
In other words, the iOS version that you’re going to get comes with this bug from the very beginning, even though Apple has been aware of it for quite some time now.
The good news is not only that an exploit requires physical access to the device, but also that iOS 13.1 appears to fix the problem. According to Apple, this update is projected to go live on September 30, so all iPhones should be patched by the end of the month.
For now, Apple has obviously remained tight-lipped on the bug, but the company doesn’t typically comment on anything that involves such discoveries.

 14 DAY TRIAL //
14 DAY TRIAL //