Documents obtained by The Intercept reveal the breadth of information US law enforcement can get from Apple's iMessage service (now rebranded as Messages) through court orders and subpoenas.
Because all iMessage content is encrypted end-to-end, not even Apple can access the actual conversations. Nevertheless, iMessage records some metadata that is sent and recorded on Apple servers.
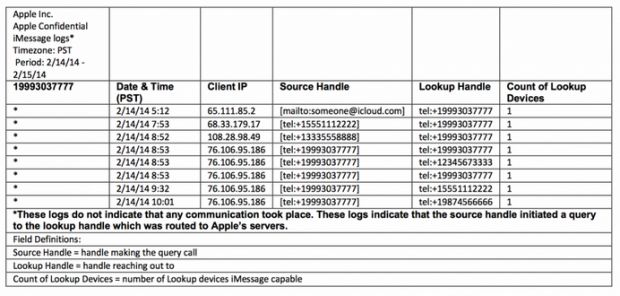
For example, Apple logs every new conversation users attempt to start. Every time a user enters a person's phone number inside the app, iMessage queries the Apple servers to determine if the other phone number belongs to an iMessage user or not. This information is used to start a conversation via iMessage or the phone's default SMS app.
iMessage metadata includes the phone owner's IP address
In the case of an investigation, law enforcement agents who obtain court orders for this data can discover who a user has been talking to, the date and time this query has taken place, and the client's IP address.
These lookups don't necessarily mean a conversation has taken place, but that the user has at least attempted to contact the other party.
Additionally, because these lookups also record the user's IP address, law enforcement, or a third-party that gets a hold of these Apple logs, can establish a user's geographical location based on the IP.
The good news is that obtaining these court orders is extremely difficult and a strenuous process.
Apple lied about keeping the data
The bad news is that Apple lied about keeping this data back in 2013 when Edward Snowden exposed the NSA spying scandal, in which it was revealed that Apple had allowed the NSA to collect metadata from its service.
In a statement following that discovery, Apple said they did "not store data related to customers' location, Map searches or Siri requests in any identifiable form."
The documents obtained by The Intercept are named "iMessage FAQ for Law Enforcement," and are some sort of manual detailing what kind of data can be collected from Apple during official investigations. These files clearly show that Apple does store location information in the form of IPs, contrary to the company's previous statements.
Confronted with the details put out in the public eye by the report, Apple has told The Intercept that these logs are only saved on their servers for 30 days, after which they're deleted, unless legal procedures mandate the company to keep certain logs until the investigation ends.

 14 DAY TRIAL //
14 DAY TRIAL //