According to ESET, popular Android stalkerware apps are loaded with vulnerabilities that endanger victims and expose the privacy and security of the snoopers themselves.
Mobile stalkerware, also known as spouseware, is a type of software that is used for silent monitoring. More often than not, they are installed onto a victim's smartphone without the their awareness. As you probably guessed, the stalker must have physical access to the victim's device in order to side-load the stalkerware. Since it requires physical contact with a device, stalkers are typically members of their victims' family, social or professional circles.
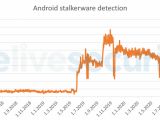
According to We Live Security's telemetry, such apps have grown in popularity over the last few years. Based on the report, there were 5 times as many Android stalkerware in 2019 compared to 2018, and 48% more in 2020 by comparison with the previous year. The privacy-invading apps can monitor the GPS location of a victim's device, as well as conversations, photographs, browser history, and other information.
Considering that they have the role of storing and transmitting data,a forensic analysis of how these apps manage data security was necessary.
To remain under the radar and avoid being labeled as stalkerware, vendors often advertise their apps as offering security to children, staff, or women. Then again, at a closer look you realize that the word spy appears frequently on their websites. Moreover, it is not difficult to find these resources online. The screenshot below is probably the most infamous example of an argument made by these apps that they track women for their protection.
More than 150 security flaws have been discovered in 58 Android stalkerware applications
At the very least, stalkerware apps promote obviously unethical activity, leading most mobile security solutions to mark them as unacceptable or dangerous. Nevertheless, given that these apps access, collect, store, and distribute more information than any other software installed, security researchers are wondering whether the apps are able to secure both general and sensitive information.
A victim is a person on whom a stalker has spied using stalkerware. On the other hand, the attacker is a third party that neither the stalker nor the victim is generally aware of. An attacker can exploit protection or privacy vulnerabilities in stalkerware or the monitoring services associated with it to gather information that can be used against both stalker and victim.
The security analysis discovered numerous critical security and privacy issues that could lead to a cybercriminal taking control of a victim's device, taking a stalker's account, intercepting the victim's data, framing the victim by uploading false information or achieving remote code execution on the victim's smartphone.
Security researchers discovered 158 security and privacy problems in 58 of these Android applications. Needless to state that they pose a significant concern on a victim's privacy. Even stalkers are not taken out of the equation, as attackers can hack their accounts and steal sensitive data.

 14 DAY TRIAL //
14 DAY TRIAL //