Windows Defender, now called officially Microsoft Defender, is becoming more and more powerful, and now a growing number of users stick with the native security protection and no longer purchase and install third-party antivirus software.
The most recent antivirus tests are living proof in this regard, as the performance of Microsoft Defender has been in line with the one of the most powerful third-party security products out there.
So right now, it makes little sense for some users to install third-party security software given that Microsoft Defender is now capable of protecting devices at OS level.
And Microsoft just doesn’t stop here. Microsoft Defender Advanced Threat Protection (Microsoft ATP) is being updated with an UEFI scanner. In other words, Microsoft’s security application can now detect malware injected in firmware, thus adding a new security layer to devices running Windows 10.
Malware-infected firmware is the most difficult to detect, as it launches before booting the operating system when security software typically launches. So in most of the cases, such malware remains undetected.
Microsoft says the UEFI scanner is built with help from chipset manufacturers, who contributed with “insights,” allowing Microsoft Defender ATP to scan the firmware filesystem and determine if a risk of malware exists or not.
“Windows Defender System Guard helps defend against firmware attacks by providing guarantees for secure boot through hardware-backed security features like hypervisor-level attestation and Secure Launch, also known as Dynamic Root of Trust (DRTM), which are enabled by default in Secured-core PCs. The new UEFI scan engine in Microsoft Defender ATP expands on these protections by making firmware scanning broadly available,” Microsoft says.
The UEFI scanner comes with three important components, namely a detection engine that can help find exploits and malicious behaviors, a full filesystem scanner that closely inspects every piece of code inside a firmware, and an UEFI Anti-Rootkit that uses the Serial Peripheral Interface (SPI) to access the firmware.
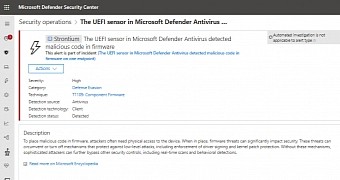
When malware is detected at firmware level, the Microsoft Defender Security Center shows more information just like for a typical infected file. An alert for compromised firmware looks like this:
“The UEFI sensor in Microsoft Defender Antivirus detected malicious code in firmware.”
“To detect unknown threats in SPI flash, signals from the UEFI scanner are analyzed to identify anomalies and where they have been executed. Anomalies are reported to the Microsoft Defender Security Center for investigation,” Microsoft says.
Microsoft explains that the UEFI scanner is just a natural evolution of all security improvements in Microsoft Defender ATP, and the company says that more and more such updates are on their way.
“With its UEFI scanner, Microsoft Defender ATP gets even richer visibility into threats at the firmware level, where attackers have been increasingly focusing their efforts on. Security operations teams can use this new level of visibility, along with the rich set of detection and response capabilities in Microsoft Defender ATP, to investigate and contain such advanced attacks,” the company explains.
Microsoft Defender is offered as the default security application on all Windows 10 devices, and when installing the operating system, the antivirus engine is automatically enabled too.
Microsoft Defender can be further controlled from Windows Security, a security hub available in Windows 10 that provides access to all security features in the OS. Windows Security is also the home of other security controls, including parental tools and antivirus scanning options, while also allowing users to get more information on the current health status of their devices.
Like fully-featured antivirus products, Microsoft Defender also comes with real-time protection, cloud scanning, virus definition updates shipped on Windows Update, and multiple scanning modes.
 14 DAY TRIAL //
14 DAY TRIAL //