Symantec has identified a new crimeware kit that’s mainly designed to launch distributed denial-of-service (DDOS) attacks against companies, with the purpose of blackmailing them. It’s Dubbed Zemra, it costs only around $125 (100 EUR) and researchers believe that it has been active since June 25, 2012.
Experts reveal that Zemra is similar to other crime packs such as ZeuS and SpyEye, being controlled from the same type of panel which allows the botmaster to launch commands and view the number of infections.
Backdoor.Zemra’s main functionality is to launch DDOS attacks, but it also comes with a number of other interesting features. It’s able to monitor devices, collect system information, execute files, and even update or uninstall itself if necessary.
The malware uses 256-bit DES encryption for communicating with its command and control (C&C) server and it can spread via USB devices.
“Initially, when a computer becomes infected, Backdoor.Zemra dials home through HTTP (port 80) and performs a POST request sending hardware ID, current user agent, privilege indication (administrator or not), and the version of the OS,” Alan Neville of Symantec said.
“This POST request gets parsed by gate.php, which splits out the information and stores it in an SQL database. It then keeps track of which compromised computers are online and ready to receive commands.”
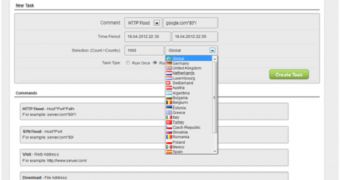
After analyzing the threat, experts determined that Zemra is able to launch two types of attack: HTTP flood and SYN flood.
The SYN flood attack is pretty much standard, a number of packets being sent to the targeted server in an attempt to cause it to run out of resources and block real users from sending it requests.
“The first type, HTTP flood, opens a raw socket connection, but has special options to close the socket gracefully without waiting for a response (e.g. SocketOptionName.DontLinger). It then closes the socket on the client side and launches a new connection with a sleep interval,” Neville explained.
“This is similar to a SYN flood, whereby a number of connection requests are made by sending multiple SYNs. No ACK is sent back upon receiving the SYN-ACK as the socket has been closed. This leaves the server-side Transmission Control Blocks (TCBs) in a SYN-RECEIVED state,” he added.
 14 DAY TRIAL //
14 DAY TRIAL //