The author of Tox crypto-malware building kit decided to get out of the business, a week after popularizing the platform for about a week on darknet and reaching the conclusion that he’s not a criminal.
News about Tox emerged last week, a ready-made platform that allows anyone to create their variant of crypto-malware and take a hefty share of ransom paid by victims.
Access to the kit and building the malware is free, but the client is the one responsible of distribution, and 30% of the profit would go to the author of Tox.
A bit late for it, but Tox does not want to be a criminal
On Wednesday, the creator of the ransomware-as-a-service platform decided to get out of the game, although it is claimed that in one week the platform recorded 1,000 users and more than 1,000 infections.
“It's been funny, I felt alive, more than ever, but I don't want to be a criminal. The situation is also getting too hot for me to handle,” Tox says on the page of the platform and in an entry on Pastebin.
Security researchers from McAfee were the first to draw attention to and analyze Tox ransomware. They concluded that the malware “lacks complexity and efficiency within the code,” suggesting that it is not the work of a skilled developer.
This is confirmed by Tox, by saying that he’s “just a teenager student,” who built the platform and virus with the help of various people via chat conversations and there is no team of hard core hackers behind the project.
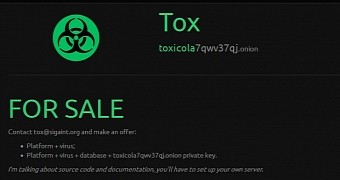
Author looking to sell database, or will unlock data for free
At the moment, Tox sits on a database of decryption keys and offers it for sale to the highest bidder. If no one makes a bid, though, he is resolute on releasing the keys and automatically unlock victim’s files.
As for the users that have already registered, they are going to receive their funds, “in the case somebody pays some of your ransoms.”
Tox ransomware may come under different names, but it poses as a Word document and has the extension SCR, an executable associated with screensaver files. When launched, the malware starts encrypting files on the hard disk and shows the ransom message upon completion.
 14 DAY TRIAL //
14 DAY TRIAL //