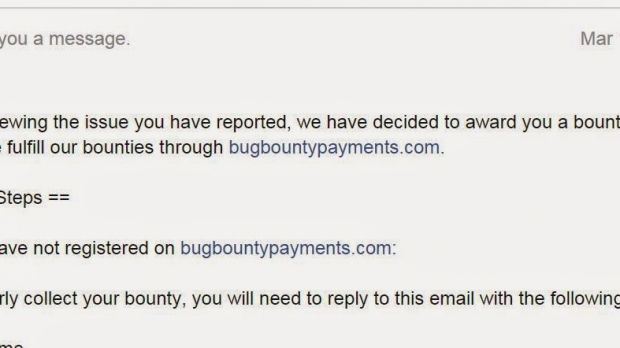
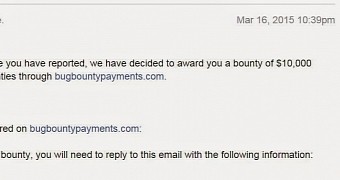
A new vulnerability discovered in Facebook system by an independent security researcher was deemed worthy of a $10,000 / €9,400 reward from the social network as it allowed a third-party app unrestricted access to all the private photos of a user.
Exploiting it required an attacker only to create an app that requested access to the private image section in the Facebook account.
This can be easily achieved since most users do not pay attention to the permissions they grant to a software product upon installing it on the mobile device.
Sync server allows access to private content
The researcher who found the bug is Laxman Muthiyah, who is also credited for another image-related glitch in Facebook, which could have been used to delete any photo album in any account of the social network; reporting this glitch earned him a bounty of $12,500 / 11,700 and a spot on Facebook’s “thank you” list for 2015.
Exposing the private Facebook photos of a user to third-party software touches on the “sync photos” feature in Facebook’s mobile app, which is enabled by default and syncs with the account up to 2GB of images from the device; this content is set to remain private until the user decides otherwise.
To synchronize the private photos, a connection with an endpoint called “vaultimages” is established via a Graph API call, based on an access token. Muthiyah found that the server was vulnerable and accepted requests from any app with permission to read mobile photos.
Facebook solves problem in 30 minutes
“The vulnerable part is, it [the endpoint] just checks the owner of the access token and not the application which is making the request. So it allows any application with user_photos permission to read your mobile photos,” the researcher explains.
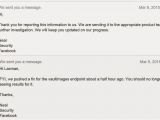
The misconfiguration of the server was reported to Facebook’s security team on March 9, and the hole was plugged in less than half an hour from validating the submission, the researcher says.
The fix consisted in simply creating a list of official Facebook apps that are accepted by the server for reading synced content.
On March 16, Muthiyah received an email informing him of the monetary reward issued in his name.
A video demonstrating the glitch has been created by the developer.
 14 DAY TRIAL //
14 DAY TRIAL //