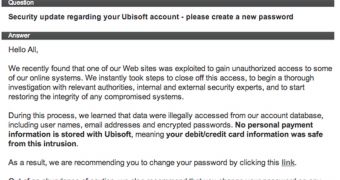
On Tuesday, Ubisoft admitted that its Uplay database was hacked. The company says the attackers have gained access to usernames, emails, and encrypted passwords. Fortunately, financial information has not been compromised.
A large number of high-profile companies have been hacked lately. The fact that Ubisoft joins their ranks isn’t very surprising.
However, experts say they’re not entirely happy with the way Ubisoft is handling the disclosure. Furthermore, the company’s password encryption practices are questioned.
Avira Security Expert and Product Manager Sorin Mustaca has shared some insight with Softpedia regarding the Ubisoft hack.
The expert believes that there are two likely scenarios that led to the breach: - the software running on these systems was vulnerable and the criminals exploited the vulnerability; - the cybercrooks got possession of login credentials of some Ubisoft employee(s) and have used them to get the data.
“Using dedicated attacks (social engineering, spear phishing, targeted malware, ‘water-holing’ attacks) against employees, probably computers inside Ubisoft got infected and unsuspicious employees got their credentials stolen. Getting valid credentials is sometimes easier to achieve than exploiting vulnerabilities,” Mustaca explained.
However, the following statement from Ubisoft is what worries Mustaca and other experts the most:
“Passwords are not stored in clear-text but as an obfuscated value. These cannot be reversed but could be cracked, in particular if the password chosen is weak.”
“This tells me that most probably the password were just hashed using an algorithm like MD5. The de-facto standard these days is to use SHA256 and a salt,” Mustaca noted.
Security expert Graham Cluley agrees.
“That doesn’t sound very comforting to me, and suggests that Ubisoft may not have been following best practice to secure those passwords. Fingers crossed, hackers don’t manage to crack the passwords… That would make a bad situation even worse,” Cluley said.
Trend Micro’s Rick Ferguson calls the breach notification a “fail.” Not just because the company doesn’t clearly explain which type of encryption it’s using, but also because it has included a link in the emails sent out to impacted customers.
“If you as an organisation ever have the misfortune to have to notify your customers of a breach, never include a link in the reset mail, it encourages insecure behaviour in your customer base and leaves them wide open to the inevitable phishing attacks that always follow this kind of event,” Ferguson said.
So, the best thing Ubisoft customers can do is change all their passwords that are the same as the one used for uPlay. Changing only the Uplay password is not enough in the likely event that the compromised hashes can be easily cracked.
 14 DAY TRIAL //
14 DAY TRIAL //