A recent research focused on understanding the financial losses companies incur in their actions to stifle cyber-attacks reveals that an average of $1.27 / €1.09 million per year is wasted on dealing with false positive security alerts.
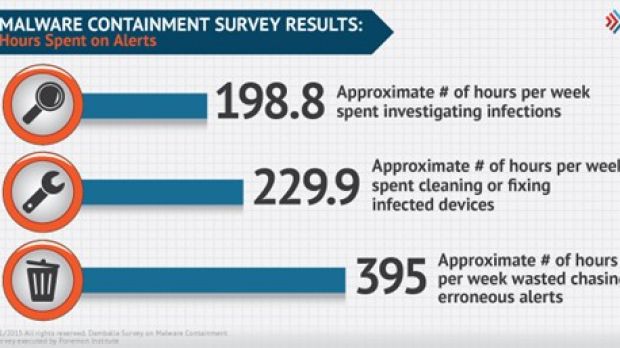
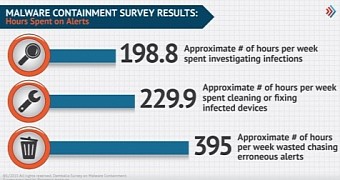
According to the study carried out by the Ponemon Institute and published this month, business organizations spend almost 200 hours per week investigating infections and almost double the time is wasted with chasing erroneous alerts.
Less than half of the companies rely on automated systems
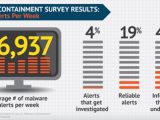
About 17,000 malware alerts are typically received in a week by the entities that participated in the study and only 3,218 (19%) are deemed reliable. Out of these, only 705 are actually investigated, which amounts to 4% of the total malware warnings recorded.
One conclusion that can be drawn from these figures is that the companies do not have proper systems to detect serious cyber-attacks, which would lower the number of false positive alerts and allow the security department to focus efforts on the alerts that could lead to compromise.
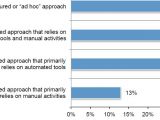
From the answers received by the Ponemon Institute, it appears that a third of the organizations have an unstructured approach to responding to cyber incidents and 40% of them said that they did not have a certain individual responsible for fending off malware hurled at their systems.
In the more fortunate cases, the companies had the necessary assets for automatically sifting through the alerts and gathering intelligence on the risk posed by the detected malware. However, this is valid for only 41% of the questioned companies.
Companies should have tools that detect relevant threats
The report has been commissioned by Damballa, a company providing automated breach detection solutions for enterprises, and it includes information compiled from 630 IT an IT security practitioners in the US.
“For years, the mantra has been to prevent attackers from getting into the network. While that is necessary, it isn't effective against advanced threats. Prevention technologies rely on prior knowledge of a threat and today's adversaries don't come with a calling card,” Brian Foster, Damballa CTO, said via email.
He added that if prevention tactics fail, then securing the affected systems turns into a race against time, and unless adequate resources and focus are allotted, the problem cannot be mitigated.
“I suggest you prevent what you can, be prepared to detect what you can't prevent, and be sure you can rapidly respond to infections that matter,” Foster concluded.
On January 20, at 10 AM (PT), Damballa will hold a webinar discussing the findings of the report.
 14 DAY TRIAL //
14 DAY TRIAL //