A malicious campaign believed to be targeted in nature and initiated by Chinese cyber spies has been discovered by security researchers to affect Forbes.com.
Signs of nefarious activity on the highly popular domain were detected by security researchers for a short period of time last year, between November 28 and December 1.
Flash Player and Internet Explorer vulnerabilities leveraged
Due to lack of visibility, security company iSIGHT Partners, which traced the campaign together with Invincea, does not discard the possibility that the threat actor operated during a longer time frame.
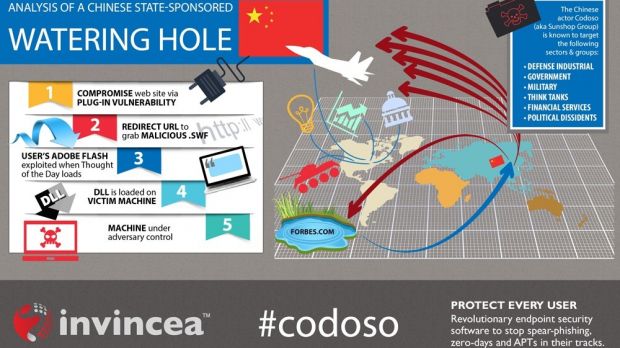
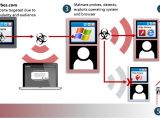
According to the researchers, the attackers compromised the Flash-based “Thought of the Day” quotation widget that is displayed when a Forbes.com page loads, and their way in was a Flash Player vulnerability, CVE-2014-9163, patched on December 9, 2014.
Invincea says that iSIGHT Partners’ analysis discovered that the exploit passed by the threat actor to vulnerable machines also included a then zero-day glitch (CVE-2015-0071) in Internet Explorer.
This one has been patched with the release of this month’s Patch Tuesday updates from Microsoft and it allows bypassing the Address Space Layout Randomization (ASLR) protection in IE 9 and higher. On systems running earlier builds of the web browser, the attack would be successful with the Flash Player exploit alone.
Operation attributed to Chinese hackers
Based on historical information gathered by iSIGHT Partners security researchers, the attack was attributed to a group of Chinese hackers called Codoso, also known by the name Sunshop Group.
“Malware leveraged in the incident included resources written in simplified Chinese and bore a resemblance to variants of Derusbi, malware unique to Chinese cyber espionage operators,” iSIGHT said on Tuesday.
Adding to correct attribution was the fact that the command and control (C&C) domain used for the operation made passive connections to a domain associated with the Codoso team.
Despite the huge traffic Forbes.com enjoys, the researchers believe that the nefarious activity targeted specific entities, US defense contractors and financial institutions being among them.
While tracking the movements of the group, the researchers observed that the Chinese hackers targeted individuals connected to government, military, defense, financial and energy sectors, as well as think tanks covering foreign affairs and political dissident groups.
 14 DAY TRIAL //
14 DAY TRIAL //