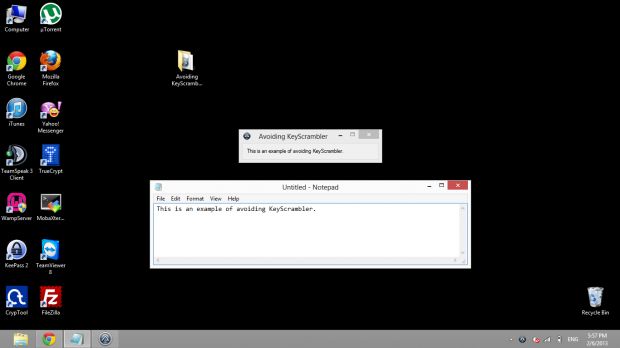
Many users rely on KeyScrambler to protect themselves against keyloggers, the pieces of malware designed to log keystrokes in an effort to steal sensitive information from infected computers. However, security researcher Dragoş Gaftoneanu says the application is not as efficient as it should be.
The expert has identified a way to bypass the protection offered by the software.
“Windows allows it’s applications to interact with one another. That’s why you can read the text from every input of every application under certain conditions,” Gaftoneanu explained in a blog post.
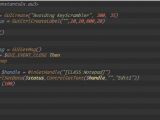
“To avoid KeyScrambler and log the keys the user presses, you need to create a script to hook yourself on the application you want by using handles. When a user presses a key, you read the value of the active input as a string and get the last character from it. That’s the key the user pressed.”
The researcher has developed a script to demonstrate his findings and he has provided Softpedia with a screenshot which shows the script in action.
We’ve reached out to QFX Software Corporation, the company that develops KeyScrambler, to see what they think about Gaftoneanu’s findings.
“One thing to clarify is that as a keystroke encryption program against keyloggers, KeyScrambler simply can't protect things outside of its designed scope of protection. The researcher's assumed attack, while interesting, can hardly be called keylogging,” said Qian Wang, the CEO of QFX Software Corporation.
“It's almost the same as saying that after you've saved a Word document, then have some code to read the document and claim it's KeyScrambler's fault. Some Windows programs make it possible to read the contents of certain user interface elements, so one can read the content of what's been typed,” he added.
“But not all applications nor all UI elements are as vulnerable to the researcher's attack. I'd be curious to see if the researcher's attack actually works in all programs against KeyScrambler,” Wang noted.
“As you know, there are no security programs that can protect you in every single situation, and that's why we have made KeyScrambler compatible with most security programs and tokens and smart cards, for layered security.”
He has highlighted the fact that KeyScrambler has proven itself to be highly effective against a wide range of keyloggers in tests performed by independent companies.
“We believe KeyScrambler is a valuable layer of defense for PCs. We've been improving it over the years and KeyScrambler 3.0 will be out later this week,” the CEO concluded.
 14 DAY TRIAL //
14 DAY TRIAL //