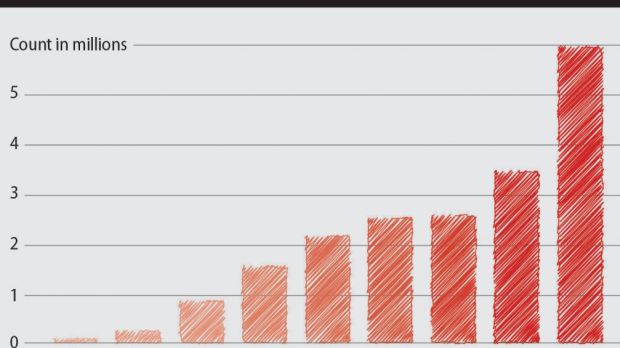
A fresh report on the state of new malware strains recorded in the second half of 2014 reveals that cybercriminals have doubled their efforts in producing threats, as the amount of new strains grew to 125% based on statistics from a security company.
All samples assessed for the research were detected via virus signatures and consisted in deviations from a previous variant belonging to a certain malware family.
Cybercriminals make small changes to known malicious pieces specifically to evade detection signature-based detection. A modification can, in some cases, lead to a successful compromise of a victim’s computer.
H2 2014 sees 125% increase in the number of malware variants
Telemetry data from German security vendor G Data shows that the second part of 2014 broke all previous records as far as new malware is concerned.
The total number of new malware samples identified by security vendor G Data in 2014 was 5,998,685, but more than half (4,150,068) occurred in the second part. Putting it differently, a new malware sample emerged every 3.75 seconds.
At the top of the list are adware variants, whose number G Data says it accounted for 31.4% (almost five times more than in the first part of the year) of all the threats the company created signatures for. Basically, “almost one in three new detections came from this sector,” the researchers say in a report published this week.
Banking Trojans target the US, Canada and the UK
One of the most prevalent banking Trojans found by G Data is Vawtrak, a piece that is constantly updated by its authors with minor modifications, and which made thousands of victims in Canada.
According to the report, security solutions deflected 44.5% more banking malware in 2014 than in the previous year. The analysis of the 25 most targeted financial institutions shows that 72% of them were from the US (36%), the UK (24%) and Canada (12%).
Bank of America was the most prevalent target in banking Trojan's configuration files, followed by Citi and PayPal.
“In total, there were seven new targets in the Top 25, including one French bank, two Russian banks, a Russian payment service, two banks from the UK and a bank from Canada,” the report states.
Surprisingly, the research did not include results for ransomware with file encrypting capabilities, a malware type that brings a hefty profit to cybercriminals.
Between February and April this year, the operators of TeslaCrypt made $76,500 / €66,500. However, older pieces of similar threats are responsible for millions of dollars in losses.
 14 DAY TRIAL //
14 DAY TRIAL //