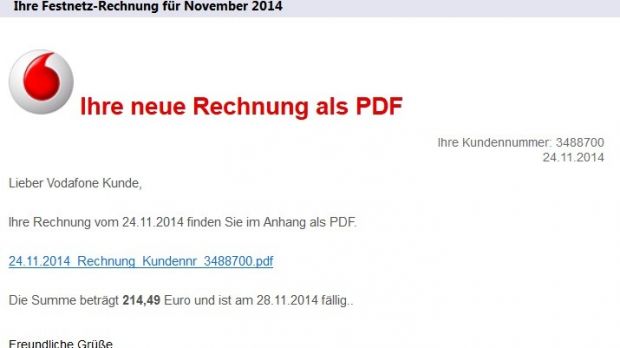
A phishing campaign targeting German users relies on emails claiming to be from reputable companies like Vodafone, Telekom and Volksbank to spread malware.
The messages are written in German and purport to deliver an invoice, pointing the recipient to an address where the malicious software sample is hosted.
Researchers at AVG said that the campaign started earlier this year, when it targeted Germany in particular. Recently, though, they have observed that the actors behind it have taken the operation to a higher level and now send the emails to users all over the world.
Download link is unique for each malware version
Interestingly, they did not change the language of the message, so the targets are still German speakers, making the scam easier to detect by all the other recipients.
Changes exist, however, as the email includes a current date stamp, a random customer number, and a different payment amount. This is designed in particular to evade filtering of anti-spam systems.
Jakub Kroustek of AVG says that the cybercriminals spoof the email address in order to make the invoice delivery seem legitimate; but by looking at the reply address or checking the source of the email, the recipient could easily detect the scam.
In one of the cases, though, the domain used for sending the fake communication had a Romanian TLD (top-level domain), which should ring the alarm since the message claims to come from a German company, and the author did not even bother to hide it.
Kroustek says that the malware variants have their own download link, leading to a ZIP archive hosted on a compromised website.
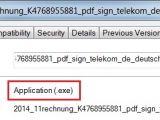
The double extension is used for tricking the victim into believing that the file is a document of some sort (generally PDF), when it is actually an executable item.
Steganography is employed, anti-debugging mechanism available
Another interesting fact is the use of steganography, which implies storing the malware in a different file, in this case inside a GIF image. Once executed, the code is decrypted and placed in a new process.
The following stage of the infection consist in achieving persistency on the affected system by registering the malicious process to be run with the operating system.
The malware authors have implemented modules for detecting a virtual environment, which would suggest that an analysis of the threat is attempted.
It appears that the GIF image includes another malicious executable, which relies on the same anti-debugging techniques as the initial sample.
In order to remain stealthy on the system, the malware does not act immediately after the Windows machine is started, and waits for half an hour before taking the first action.
Commands are delivered via codes
The AVG researcher found a set of command and control (C&C) servers and determined that the threat sends the name of the computer, the version of the operating system, CPU-related information (including the number of cores), and memory details.
Once the data is received, the C&C server sends out codes corresponding to specific commands to the compromised system. Everything is delivered via an encrypted connection.
The commands include opening web pages, downloading and executing specific files, terminating the malicious activity or putting it into standby for a certain amount of time.
If the user is vigilant, which is more necessary now than at any other time of the year, they can avoid getting infected. A peek at the source to check the reply address or multiple grammar mistakes are sure signs of a scam.
 14 DAY TRIAL //
14 DAY TRIAL //