Anti-Spam
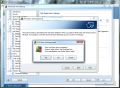
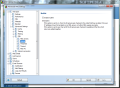
As any respectable security suite, AVG’s product offers protection against the nagging spam messages reaching our inbox. Despite an email client’s set of rules for filtering your messages so that the inbox folder receives as little unwanted mails as possible, redirecting them to the junk folder instead, having an additional anti-spam solution does not hurt. AVG Internet Security 9 can check and mark as spam email in three major email clients: Microsoft’s Outlook (we used 2010 beta), Mozilla Thunderbird and The Bat!. All three of them are extremely reliable and widely spread among computer users.
The spam-detecting algorithms in AVG verify the POP3 email flow for any unwanted messages, marking the suspected ones with SPAM in their subject (you can replace this with any other string may please you). As nothing is attached to the email client (AVG simply monitors the folders where the new messages are downloaded and checks out the new items), sorting AVG-detected spam is up to the filtering capabilities of the client of your choice.
Working with the default settings of AVG’s anti-spam component did not make too good of an impression, as there were plenty of valid messages labeled as spam, and enough spam passed as legitimate email. The test we faced the feature with consisted in simply letting the anti-spam do its job on a valid email account and mark the spam according to the default anti-spam filter. With this configuration, AVG managed to mark over 100 messages as spam, out of a total of 644. This is not a very encouraging number.
But the odd thing is that after adjusting the filter to learn that a particular message was wrongfully labeled as unwanted, and then sending the exact same message to the monitored account, AVG still treated it like spam. Further testing in this sense resulted in the same outcome.
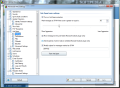
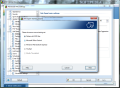
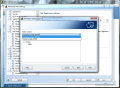
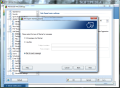
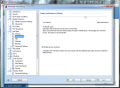
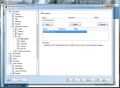
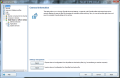
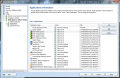
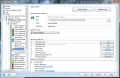
Anti-Spam module in AVG Internet Security 9 provides the largest number of settings in the entire application showing the full versatility of the product. Besides spam training, which proved to be amiss in our case, there is the possibility to define a Realtime Blackhole List (RBL) server to be queried when analyzing downloaded messages, setting up lists of approved email addresses, as well as blacklisted ones, both of which working just great and having import/export support (TXT, Windows Address Book, WAB file or Microsoft Office Outlook), making your life easier.
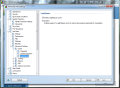
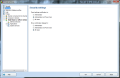
And this is not all, as the component provides some settings for the advanced users to feast with. The advanced settings available for the module are truly designed for those knowing exactly how to handle them and no other help will be available save for on-the-spot hints. The fine filtering supplied by these configuration options includes filtering by language, country, setting up list of approved/blocked IPs and spoofed senders (blocks spammers that spoof your domain name).
And the filtering goes on with finer tuning of RBL, giving you the option to add the servers yourself, enable multihit, threshold, maximum number of IPs queried against RBL servers or timeout limit for finishing all RBL interrogation. All these settings definitely do not address the home user for whom AVG Internet Security has been created, and rather target network administrators handling email servers.
Firewall
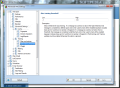
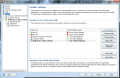
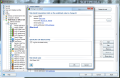
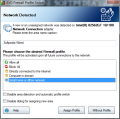
The firewall present in the suite benefits from its own settings and configuring it straight from the main interface limits you to selecting a different profile (SOHO network, allow/block all apps, computer in domain or direct connection to the Internet), enabling or disabling the firewall and starting emergency mode, which blocks absolutely all Internet traffic.
The screen of the Firewall component will also show some brief information about the amount of time the firewall has been enabled for or the amount of packets it blocked (real-time count). However, the real configuration settings are to be found under the “Tools” menu. In contrast to anti-spam configuration, the firewall can be easily set up by any user.
Provided that you have already configured the module upon installing the security suite, there is nothing else left to do except for creating a rule when a new application that is not on AVG’s whitelist launches. In that case, you get to grant permission to run or block it. But things are a tad more complicated because AVG’s firewall works according to the profiles set by the user. This means that the applications will be permitted/denied connection depending on the currently used profile.
AVG’s firewall automatically detects the new networks you connect to and will prompt you with the profile switch dialog. If you keep connecting only to safe networks, you can disable area detection and automatic profile switch.
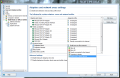
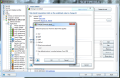
In order to make the module as non-intrusive as possible, the developer added a database of trusted applications. Its usage can be toggled for any of the profiles available. If you take a look at the firewall settings under the “Tools” menu, under Applications, you’ll see all the programs that have been verified by AVG and the action taken.
If you are displeased with AVG’s application management, you can take the matter into your hands and create your own rules to be applied for each software in the list. Rule details permit changing the protocol used, direction of the connection, communication ports (both local and remote) and remote address connection. Although this comes down as extremely complicated for the average user, AVG’s firewall provides the means to customize the way an application connects outside your computer.
AVG’s firewall proved to be reliable enough to stealth all the ports on the computer, meaning that a possible attacker could not find the ports to tap into your system. These were not shown as closed, but rather put under the invisibility cloak, which is for the win. But as this is not all a firewall should do, we proceeded to data leakage tests to see whether information is safe on the system or can easily drain away even with AVG’s firewall on guard. The results obtained were average, with some tests managing to be astute enough to fool the firewall, while others were immediately reported.
Trusted applications database makes AVG’s firewall one of the most non-intrusive security applications on the market. Thanks to this whitelist, you won’t have to deal with nasty dialogs asking you what should be done with a recently launched app that requires Internet connection. However, if you start a program that is not on AVG’s safe list, you will have to take the decision yourselves.
 14 DAY TRIAL //
14 DAY TRIAL //