- Server related
- By Catalin Cimpanu
- October 18th, 2016
Magento Malware Uses Steganography to Steal Payment Card Data
Malware hides credit card data inside image files
- Security
- By Catalin Cimpanu
- July 28th, 2016
Malvertising Campaign Infected Thousands of Users per Day for More than a Year
Campaign affected 22 ad networks, 113 legitimate sites
- Security Blog
- By Catalin Cimpanu
- April 22nd, 2016

Malware Coders Find the Perfect Technique to Help RATs Avoid Detection
Crooks use fileless malware combined with steganography
- Security
- By Catalin Cimpanu
- November 19th, 2015
Malware Turns to DNS and Steganography to Hide C&C Communications
Malware operations evolve in a clever way
- Security Blog
- By Catalin Cimpanu
- November 4th, 2015

Hackers Cleverly Hide Backdoor Inside the EXIF Data of a Joomla CMS Logo
Clever technique, but not clever enough to avoid detection
- Security
- By Catalin Cimpanu
- July 30th, 2015
HAMMERTOSS Malware Uses Twitter and GitHub to Disguise Its Activity
FireEye researchers attribute it to Russian group APT29
- Security
- By Ionut Ilascu
- July 6th, 2015
Infections with ZeusVM Banking Malware Expected to Spike As Building Kit Is Leaked
Source code for control panel has also been leaked
- Security
- By Ionut Ilascu
- June 26th, 2015
Trojan Hiding in PNG Images Hits Healthcare Organizations
Crooks resort to steganography and fileless malware methods
- Virus alerts
- By Catalin Cimpanu
- June 16th, 2015
Stegoloader, the Malware That Hides in Image Files
Stegoloader can hide its source code inside a plain PNG file
- Security
- By Ionut Ilascu
- March 25th, 2015
Vawtrak Trojan Hides Updated Server List in Website Icons
Over 13,000 Canadians affected by recent Vawtrak campaign
- Security
- By Ionut Ilascu
- January 19th, 2015

Siri’s Voice Could Carry Sensitive Info to an Attacker
Researchers draw attention to steganography-based attacks
- Security
- By Ionut Ilascu
- August 9th, 2014

Lurk Malware Dropper Hides Remote Server Links Inside Images
The use of steganography makes detection of malware information more difficult
- Security Fixes and Improvements
- By Eduard Kovacs
- January 20th, 2014
BitTorrent Creator Working on Tool That Hides Secrets in Inconspicuous Files
Bram Cohen is collaborating with a team from Stanford on the project
- Security Blog
- By Ionut Ilascu
- November 29th, 2013

JPEGs Leveraged for Targeted Attacks
Images contained encrypted configuration files and binaries
- Windows software reviews
- By Ionut Ilascu
- October 30th, 2013
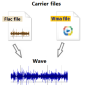
Hide Data Within Audio Files
DeepSound can encode secret files in FLAC, WAV, and WMA audio
- Web Blog
- By Lucian Parfeni
- April 10th, 2013
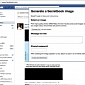
Secretbook Encodes Hidden Messages in Facebook Photos
The Chrome extension makes it possible to share messages discreetly
- Windows software reviews
- By Ionut Ilascu
- February 27th, 2013
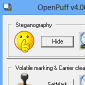
Professional Data Obfuscation Tool
It can split data across multiple carriers, 3-password protection