- Security
- By Sergiu Gatlan
- November 9th, 2018

Cryptomining Malware Uses Rootkit to Hide on Infected Linux Systems
Monero miner obfuscates himself from most monitoring tools
- Security
- By Sergiu Gatlan
- September 28th, 2018

Fancy Bear Attacks Governments Using LoJax UEFI Rootkit
Attacks can be blocked by enabling Secure Boot
- Security Blog
- By Catalin Cimpanu
- October 19th, 2016
MBRFilter Protects Computers from MBR Malware and MBR Ransomware
Cisco releases MBRFilter as free download utility
- Security
- By Catalin Cimpanu
- September 25th, 2016

Street Fighter V Update Opens Backdoor on Windows PCs
Capcom rolls back game update after fan anger
- Virus alerts
- By Catalin Cimpanu
- September 5th, 2016

Pokemon-Themed Umbreon Rootkit Targets Linux x86 and ARM Platforms
Rootkit lets hackers open SSH connections to victim's device
- Virus alerts
- By Catalin Cimpanu
- February 12th, 2016

HummingBad Android Malware Is a Dangerous Rootkit with a Bright Future
Android malware comes with rootkit component to show ads
- Security
- By Catalin Cimpanu
- January 27th, 2016

VirusTotal Adds Support for Scanning Malicious Firmware Images
Users can utilize it to detect rootkit malware
- Virus alerts
- By Catalin Cimpanu
- October 6th, 2015

HDRoot Bootkit Impersonates Microsoft's Net Command
HDRoot is the work of the Winnti APT group
- Security
- By Ionut Ilascu
- June 2nd, 2015
Older Macs Exposed to Rootkit Installation via Zero-Day Bug in Firmware
Attack is as dangerous as Thunderstrike but easier to pull
- Security
- By Ionut Ilascu
- May 11th, 2015

New Malware Pieces Run Completely on Graphics Card
Proof-of-concept code is now publicly available
- Security
- By Ionut Ilascu
- April 9th, 2015
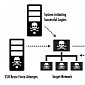
Group Uses over 300,000 Unique Passwords in SSH Log-In Brute-Force Attacks
SSHPsychos regroup after takedown operation
- Security
- By Ionut Ilascu
- September 29th, 2014
Pirate Bay Serves Malicious Advertisements
Angler exploit kit used to deliver the malware
- Security
- By Ionut Ilascu
- September 4th, 2014
Four New Malware Samples Emerge Every Second
More than 31 million new threats appeared in Q2 2014
- Security Blog
- By Ionut Ilascu
- June 14th, 2014

BlackEnergy Trojan Sample Designed for Windows 8 and Up
Malware not signed, less capable to infect modern Windows
- Virus alerts
- By Eduard Kovacs
- February 28th, 2014
Gameover Borrows Kernel-Mode Rootkit from Necurs Malware
Security researchers from Sophos have analyzed the new version
- Virus alerts
- By Eduard Kovacs
- November 1st, 2013

BadBIOS Malware: Reality or Hoax?
Facts and questions regarding a piece of malware that appears to be out of a Sci-Fi movie
- Security Blog
- By Eduard Kovacs
- September 23rd, 2013
Download ESET Rootkit Detector for Mac
Some Mac malware has also been spotted using rootkit techniques