- Security
- By Eduard Kovacs
- March 12th, 2013

McAfee Launches Whitelisting Solution for Android-Based Embedded Systems
The application offers a higher level of protection because it resides in the kernel
- Security Blog
- By Eduard Kovacs
- March 12th, 2013

Pop-Up Browser Flaw Allows Hackers to Bypass Lock Screen on Samsung Phones – Video
Samsung Galaxy S III and Note II are known to be affected
- Security Blog
- By Eduard Kovacs
- March 1st, 2013

F-Secure Launches Safe Avenue Multi-Device Offering
Safe Avenue has benefits for both consumers and operators
- Security Blog
- By Eduard Kovacs
- February 27th, 2013
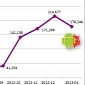
Commtouch Report: 178,246 Pieces of Android Malware Collected in January 2013
The company has released its February 2013 Internet Threats Trend Report
- Security Blog
- By Eduard Kovacs
- February 26th, 2013

MWC 2013: “Hackers” Protest Against Kaspersky – Video
The security firm has come up with a clever way to advertise its products
- Security Blog
- By Eduard Kovacs
- February 25th, 2013

MWC 2013: General Dynamics Demos GD Protected Software on LG Optimus 3D Max
The defense contractor promises highly secure mobile devices
- Security Blog
- By Eduard Kovacs
- February 22nd, 2013
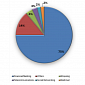
In 2012, Trend Micro Identified 4,000 Phishing URLs Designed for Mobile Web
Most of the malicious sites replicated the ones of financial institutions
- Security
- By Eduard Kovacs
- February 21st, 2013

Symantec and G&D Team Up to Develop Protected Mobile Security Applications
Symantec's products will leverage the Trusted Execution Environment
- Security Blog
- By Eduard Kovacs
- February 20th, 2013

AVG Provides Three Quick Tips to Protect Your Devices During the Winter Break
Passwords, anti-theft and safe browsing are the key to a peaceful vacation
- Security Fixes and Improvements
- By Eduard Kovacs
- February 18th, 2013

Defense Contractor BAE and Vodafone Enter Cybersecurity Partnership
The first order of business is the Vodafone Mobile Threat Manager
- Security
- By Eduard Kovacs
- February 18th, 2013

Data from the RAM of Android Devices Can Be Read by Putting Them in the Freezer
Researchers from the Erlangen University have developed an attack called FROST
- Security Blog
- By Eduard Kovacs
- February 8th, 2013
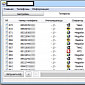
Spammers Use Tool to Harvest Phone Numbers
Webroot experts have analyzed the latest version of the application
- Security Blog
- By Eduard Kovacs
- February 1st, 2013
Malware Served on Google Play Jumps from the Smartphone to the PC
Kaspersky experts have analyzed this particular backdoor
- Security Blog
- By Eduard Kovacs
- January 31st, 2013

All You Need to Know About Managing Your Mobile Privacy – Infographic
Mobile malware isn't the only thing you should be concerned about
- Security Fixes and Improvements
- By Eduard Kovacs
- January 31st, 2013

Kaspersky Launches Endpoint Security for Business
The security firm has released its new flagship product for enterprises
- Security Blog
- By Eduard Kovacs
- January 23rd, 2013

Cybercriminals Compromise Legitimate Websites to Distribute SMS Trojans
Experts from security firm Webroot have analyzed this campaign
- Security Blog
- By Eduard Kovacs
- January 23rd, 2013
Security Experts Warn About Fake “Temple Run 2” for Android
As the release date draws near, malicious versions will likely appear