- Security
- By Sergiu Gatlan
- November 28th, 2018
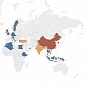
Threat Group Uses CAD Malware to Compromise Energy/Automotive Targets
The industrial espionage group is active since at least 2014
- Incidents
- By Catalin Cimpanu
- August 17th, 2016

Industrial Espionage Hackers Targeted 130 Companies in More than 30 Countries
Crooks deployed the HawkEye spywre for their attacks
- Security
- By Catalin Cimpanu
- July 25th, 2016

Ancient Hackhound Password Stealer Used in Industrial Espionage Campaign
Crooks used ISR Stealer, a modified version of Hackhound
- Online Surveillance
- By Gabriela Vatu
- January 27th, 2014

Snowden: NSA Is Involved in Industrial Espionage
Even if the data won't help national security, it is collected for commercial purposes, files indicate
- Virus alerts
- By Eduard Kovacs
- July 18th, 2012

Madi Malware: Another Trojan Targets Organizations from the Middle East
Unlike Stuxnet and Flame, Madi relies on social engineering to infect computers
- Security Blog
- By Eduard Kovacs
- July 17th, 2012

China Has Access to 80% of Telecoms via Huawei and ZTE Devices, Experts Say
The two companies are currently investigated by the US House Intelligence Committee
- Virus alerts
- By Eduard Kovacs
- June 21st, 2012
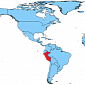
Industrial Espionage: Chinese Malware Steals Tens of Thousands of AutoCAD Files
ACAD/Medre.A has mainly impacted computer users from Peru
- Security
- By Eduard Kovacs
- November 16th, 2011

French Nuke Company Fined After Hacking Greenpeace
The organization will pay Greenpeace around half a million for damages
- Hacking News
- By Eduard Kovacs
- October 31st, 2011

Canadian Potash Industry Targeted by Hackers
'Wetware' proves itself to be once again the weakest link
- Security
- By Lucian Constantin
- September 15th, 2010

Stuxnet Industrial Espionage Malware Exploits Not One but Four Windows Zero-Day Vulnerabilities
- Security
- By Lucian Constantin
- July 16th, 2010

Signed Malware Used Valid Realtek Certificate
Targeted SCADA system had hard-coded database login details
- Mobile World
- By Ionut Arghire
- February 19th, 2009

WM-Powered Phone with Secret Software Installed Gets Stolen
Microsoft faces industrial espionage threat as a result of the incident