- Security
- By Sergiu Gatlan
- December 11th, 2018

Novidade Exploit Kit Actively Targeting SOHO and Home Routers
Malware campaign uses CSRF to change routers' DNS settings
- Security
- By Bogdan Popa
- January 12th, 2017

ShadowBrokers Now Selling Windows Exploits (Including a 0-day) for 750 Bitcoin
Pack of tools exposing Windows users now sold online
- Security
- By Bogdan Popa
- December 8th, 2016

Flash Player Security Flaws Used in Most Exploit Kits, Security Research Shows
Exploit kits attempt to take advantage of Flash Player vulnerabilities, not only in Windows, but also in Linux and Mac
- Security
- By Catalin Cimpanu
- October 2nd, 2016

Neutrino Exploit Kit Activity Slows Down to a Trickle
Is Neutrino shutting down or going private?
- Security
- By Catalin Cimpanu
- September 30th, 2016

Sneaky JavaScript Waits for User Interaction Before Infecting Them with Malware
Malicious code disguised as jQuery plugin
- Security
- By Catalin Cimpanu
- September 28th, 2016

RIG Surpasses Neutrino to Become Today's Most Active Exploit Kit
There's a new sheriff in town and his name is RIG
- Security
- By Catalin Cimpanu
- September 18th, 2016
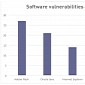
Exploit Kits Feed Off Flash Bugs, but One IE Vulnerability Is Their Favorite
CVE-2013-2551 is the most popular vulnerability with EKs
- Security
- By Catalin Cimpanu
- September 4th, 2016

Sundown Is Just a Bunch of Exploits Stolen from Other Exploit Kits
Sundown EK fails to improve market share among fellow EKs
- Security
- By Catalin Cimpanu
- September 1st, 2016

Massive Malvertising Campaign Shut Down by Cisco and GoDaddy
Crooks were installing CrypMIC ransomware via Neutrino EK
- Security
- By Catalin Cimpanu
- August 30th, 2016

Mystery Solved: Angler Exploit Kit Was Developed by Now-Arrested Lurk Gang
Angler EK was a small part of the huge Lurk infrastructure
- Cyber Espionage
- By Catalin Cimpanu
- August 12th, 2016

HOMEKit Office Exploit Generator Links Five Cyber-Espionage Campaigns
Eventually all loose ends are tied up and crooks caught
- Security
- By Catalin Cimpanu
- July 10th, 2016

There Is a Connection Between the Lurk Arrests, Angler, and the Necurs Botnet
Email address found used for registering C&C domain names for Lurk, Angler, and Necurs infrastructure
- Security Blog
- By Catalin Cimpanu
- July 8th, 2016

Sundown Exploit Kit Rises After Death of Angler and Nuclear
Exploit kit market hasn't died with Angler, nor Nuclear
- Security
- By Catalin Cimpanu
- June 27th, 2016

Nuclear Exploit Kit Shuts Down As Researchers Probe Its Infrastructure
Nuclear EK shut down a month before the Angler EK
- Security Blog
- By Catalin Cimpanu
- June 13th, 2016

Zerorose Project Shows You What Exploit Kits See
Project helps users update vulnerable software
- Security
- By Catalin Cimpanu
- June 11th, 2016

All Clues Point to the Death of the Angler Exploit Kit
Angler EK spotted online for the last time on June 7
- Security
- By Catalin Cimpanu
- June 4th, 2016

Microsoft: Flash Content Found on 90 Percent of All Malicious Web Pages
Microsoft issues a list of ten cyber-security trends