- Security Fixes and Improvements
- By Eduard Kovacs
- June 12th, 2013

Trend Micro Launches Web App Security Offering
The security-as-a-service solution is based on technology from two recently acquired firms
- Security Blog
- By Eduard Kovacs
- June 1st, 2013

Trend Micro Infographic: Are You Safe Online?
The security firm analyzes how cybercriminals catch up with the digital landscape
- Security Blog
- By Eduard Kovacs
- June 1st, 2013

Android Devices May Have up to 11 Vulnerabilities – Infographic
Trend Micro analyzes the security of Android smartphones and tablets
- Security Blog
- By Eduard Kovacs
- May 31st, 2013

Trend Micro Releases Report on Windows 8 and Windows RT
The study focuses on security, but it also analyzes functionality and hardware issues
- Security
- By Eduard Kovacs
- May 28th, 2013
Experts Find Multiple Security Flaws in Trend Micro’s DirectPass 1.5.0
The security solutions provider addressed three vulnerabilities
- Security Blog
- By Eduard Kovacs
- May 8th, 2013

Watch: Trend Micro CTO Shares Insight on Efficiency of Endpoint Antimalware
Raimund Genes explains what companies do to make sure malware is kept at bay
- Security
- By Eduard Kovacs
- May 3rd, 2013

Critical Infrastructures from Latin America Increasingly Targeted by Hackers
Trend Micro and OAS have released a study on the cybersecurity trends from Latin America
- Software Blog
- By Bogdan Popa
- April 30th, 2013

Download Trend Micro SafeGuard for Windows 8 Metro
Surf the Internet safely with this free app for Microsoft’s new OS
- Security
- By Eduard Kovacs
- March 12th, 2013

Trend Micro Introduces Enterprise Security and Data Protection
The solution can be used for tablets, smartphones, laptops, removable drives, and more
- Security Blog
- By Eduard Kovacs
- March 5th, 2013
Trend Micro Publishes Research Paper on Asprox Spam Botnet
The botnet is responsible for most of the DHL, US Postal Service and FedEx spam
- Security Blog
- By Eduard Kovacs
- February 25th, 2013

Trend Micro Enhances Custom Defense to Identify and Block C&C Communications
The solution will enable enterprises to better protect themselves against APTs
- Security Blog
- By Eduard Kovacs
- February 22nd, 2013
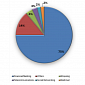
In 2012, Trend Micro Identified 4,000 Phishing URLs Designed for Mobile Web
Most of the malicious sites replicated the ones of financial institutions
- Virus alerts
- By Eduard Kovacs
- February 1st, 2013

Most of the Changes in BlackHole 2.0 Made to Evade Efforts of Security Experts
Trend Micro analyzes the evolution of the notorious exploit kit
- Security Blog
- By Eduard Kovacs
- January 31st, 2013

All You Need to Know About Managing Your Mobile Privacy – Infographic
Mobile malware isn't the only thing you should be concerned about
- Advisories
- By Eduard Kovacs
- January 22nd, 2013
Cybercriminals Use Legitimate Tools in APT Attacks, Experts Say
Trend Micro experts provide some valuable advice for IT security teams
- Security Blog
- By Eduard Kovacs
- January 15th, 2013
Real-Time Map from Trend Micro Shows Global Botnet Activity
Over 618 command and control servers found to be active over the past 14 days
- Security Blog
- By Eduard Kovacs
- January 12th, 2013

What Can Happen When Automated Homes of the Future Get Hacked – Infographic
Trend Micro on Internet-enabled devices and the associated security risks