- Security
- By Ionut Ilascu
- August 27th, 2014

Malware Pieces Use Several Techniques to Avoid Investigative Efforts
Malware authors try to send researchers on the wrong track
- Security
- By Ionut Ilascu
- August 1st, 2014
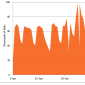
New Gameover ZeuS Variant and Shylock Rebuild Botnets
Almost 10,000 bots attempt to contact security firm sinkhole
- Security
- By Ionut Ilascu
- July 11th, 2014
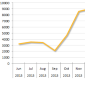
Operating Shylock Trojan Was a Full-Time Job
Developers worked from nine to five, Monday to Friday
- Security
- By Ionut Ilascu
- July 11th, 2014
Shylock/Caphaw Banking Trojan Network Disrupted
International law enforcement operation seizes Shylock command and control machines
- Virus alerts
- By Eduard Kovacs
- September 19th, 2013
Shylock Trojan Used to Target Customers of 24 Major Banks
The malware uses several tricks to avoid being detected and disrupted
- Security Blog
- By Eduard Kovacs
- August 20th, 2013
Fake Web Browser Updates Hide Sirefef/Shylock Malware
Users are advised to update software only from trusted websites
- Security Blog
- By Eduard Kovacs
- April 5th, 2013
Shakespearian Banking Trojan Shylock Starts Targets New Countries, New Sectors
Symantec experts have analyzed the latest versions of the malware
- Software Blog
- By Bogdan Popa
- January 23rd, 2013

Microsoft Blocks Even More Skype Malware
The company tries to keep users on the safe side with enhanced protection
- Software Blog
- By Bogdan Popa
- January 22nd, 2013

Microsoft Blocks Shylock Malware Spreading via Skype
The company has confirmed that its users are now on the safe side
- Security
- By Bogdan Popa
- January 17th, 2013

New Shylock Malware Infecting Skype Users
A new version of the Trojan horse is now out there in the wild
- Security Blog
- By Eduard Kovacs
- December 5th, 2012
Users Advised to Disable Smart Card for Protection Against Shylock Malware
This method is used to trick the threat into thinking that it's being analyzed
- Security Blog
- By Eduard Kovacs
- August 29th, 2012
Shylock Malware Replaces Documents with Shortcuts to Malicious Files
This is possible thanks to a component called DiskSpread
- Virus alerts
- By Eduard Kovacs
- August 8th, 2012
Shylock Trojan Injects Attacker’s Phone Number into Bank Websites
The Shakespearean virus returns with an ace up its sleeve
- Virus alerts
- By Eduard Kovacs
- February 29th, 2012
Fraudsters Rely on Live Chat Sessions to Steal Bank Accounts
Crooks take their time to chat with victims to make sure they obtain what they need
- Virus alerts
- By Eduard Kovacs
- February 21st, 2012

Shakespearian Malware Avoids Antivirus Detection
Three clever mechanisms allow it to remain undetected