- Incidents
- By Catalin Cimpanu
- October 12th, 2016
Bitcoin Wallet Blockchain.info Recovers from DNS Hijacking Attack
At the time of writing, everything is back to normal
- Cyber Espionage
- By Catalin Cimpanu
- September 14th, 2016

Nation-State Actors Are Probing Core Internet Infrastructure for Failure Points
Schneier suspects China and Russia are behind the attacks
- Virus alerts
- By Catalin Cimpanu
- June 3rd, 2016
Malware Finds New Trick to Hide Rogue DNS Settings on Windows
DNS Unlocker finds a way to hide hijacked DNS servers from human operators via one "special" character
- Security Blog
- By Catalin Cimpanu
- February 23rd, 2016

CloudFlare Launches Domain Name Registrar Focused on Security
CloudFlare-registred domain names will never expire
- Incidents
- By Catalin Cimpanu
- December 29th, 2015

UConn Website Hijacked and Used to Spread Fake Flash Player Containing Malware
University of Connecticut loses control of its DNS entries
- Security
- By Ionut Ilascu
- July 1st, 2015
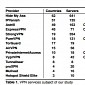
Popular VPN Services Fail to Protect User Traffic
14 commercial products tested, all vulnerable
- Security
- By Ionut Ilascu
- May 25th, 2015

Exploit Kit Delivers DNS Changer to Thousands of Routers
Router list constantly updated, at least 55 models targeted
- Security
- By Ionut Ilascu
- May 21st, 2015
Domain Registrar eNom Informs of DNS Hijacking Attack
Attack was short-lived, authorities were informed within hours
- Security
- By Ionut Ilascu
- May 19th, 2015

St. Louis Federal Reserve Forces Password Reset Following DNS Hijacking Attack
Hackers set up phishing pages to collect login credentials
- Incidents
- By Ionut Ilascu
- February 26th, 2015
Lenovo.com Domain Hijacked, Possibly by Lizard Squad
Email to company employees intercepted by the hackers
- Security
- By Ionut Ilascu
- February 23rd, 2015

Lizard Squad Diverts Connection to Google Vietnam
SSL website certificate alerts users of the trap
- Advisories
- By Ionut Ilascu
- January 28th, 2015

D-Link Routers Vulnerable to Unauthorized DNS Changing
Researcher publishes exploit code for the vulnerability
- Security
- By Ionut Ilascu
- December 19th, 2014

$20 Micro-Controller Hijacks Computer in Seconds
Teensy micro-controller turned into USBdriveby attack device
- Security
- By Ionut Ilascu
- December 15th, 2014

“Hammer Time” Break Posted on Ontario.ca Website
Clearly a prank, the attack signals admins as weak spot
- Security
- By Lucian Constantin
- August 10th, 2011


