- Games
- By Cosmin Vasile
- May 31st, 2020

The Most Anticipated Game Releases of June 2020
A month dominated by Sony's The Last of Us Part II
- Security
- By Catalin Cimpanu
- February 5th, 2016

White Hat Pwns Dridex Botnet to Push Avira Antivirus Instead of Malware
How about a free antivirus instead of some Dridex malware?
- Security
- By Catalin Cimpanu
- November 19th, 2015
Malware Turns to DNS and Steganography to Hide C&C Communications
Malware operations evolve in a clever way
- Security Blog
- By Catalin Cimpanu
- November 12th, 2015

Researcher Leverages Increased Twitter DM Size to Control Botnet
The tool allows botnet operators to manage their infrastructure without exposing their activities on their Twitter page
- Security
- By Ionut Ilascu
- March 25th, 2015
Vawtrak Trojan Hides Updated Server List in Website Icons
Over 13,000 Canadians affected by recent Vawtrak campaign
- Security
- By Ionut Ilascu
- February 26th, 2015
Ramnit Malware Infects over 500,000 in Six Months, Disables Microsoft Security Components
Anti-AV module was first seen back in 2013
- Security
- By Ionut Ilascu
- December 31st, 2014

Number of Botnet Control Servers Increased in 2014 – Report
Russian networks hosted most of the botnet control IPs
- Security Blog
- By Ionut Ilascu
- September 3rd, 2014

Rogue Code Injected in Industrial Site for Reconnaissance Purposes
Attackers possibly planning a watering hole attack
- Security Blog
- By Ionut Ilascu
- July 16th, 2014
PushDo Trojan Variant Has New Domain Generation Algorithm
More than 2,000 IP addresses connected to the researchers’ sinkhole
- Games Blog
- By Radu Haulica
- January 13th, 2014

Incoming 2014 – Command & Conquer 5
The last C&C title was cancelled in October, the future is uncertain
- Virus alerts
- By Eduard Kovacs
- August 14th, 2013

Hackers Abuse Google Cloud Messaging Service in Android Malware Attacks
Kaspersky researchers have analyzed the attacks and they've notified Google
- Security Blog
- By Eduard Kovacs
- August 7th, 2013
Malware Developers Migrate ZeuS P2P Protocol to New Port Range
Damballa experts say the 1024 – 10000 range is now used for C&C communications
- Virus alerts
- By Eduard Kovacs
- July 12th, 2013
Experts Reveal How Chinese APT Hackers Abuse Dropbox and WordPress
Cyber Squared has released an interesting report on the topic
- Security
- By Eduard Kovacs
- April 24th, 2013

184 Countries Host Crimeware Servers, Most from Asia and Eastern Europe
FireEye has released “The Advanced Cyber Attack Landscape” report
- Security Blog
- By Eduard Kovacs
- April 24th, 2013
Vernot Trojan Avoids Detection by Using Blogging Platform for C&C Communications
Drafts saved on a Japanese service are used for backdoor commands and other tasks
- Security Blog
- By Eduard Kovacs
- April 5th, 2013
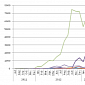
Shakespearian Banking Trojan Shylock Starts Targets New Countries, New Sectors
Symantec experts have analyzed the latest versions of the malware
- Security Blog
- By Eduard Kovacs
- February 25th, 2013

Trend Micro Enhances Custom Defense to Identify and Block C&C Communications
The solution will enable enterprises to better protect themselves against APTs