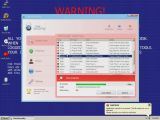
Researchers from Panda Security warn that a notorious rogue antivirus called “Total Security 2009" has started displaying ransomware behavior. In order to convince as many users as possible to pay for a useless license, the malicious application doesn't allow any file to be executed on the system.
Fake antivirus software, also known as roguware or scareware, because of the scare tactics used to advertise it, is one of the most common threats on the Internet. Because it is a highly profitable scam, cybercrooks go to great lengths in order to infect computers with it.
Pulling off a successful rogueware scheme used to require significant resources and technical knowledge, but that is not the case any longer. And as this underground market segment got overcrowded, the potential income per campaign started to decrease, forcing scammers to find innovative ways of topping the competition.
These involved developing new distribution methods, such as black hat search engine optimization or paying botnet owners to deploy them on already infected computers, and more recently starting to hold documents and computers to ransom. Rogue software that employs the latter technique is dubbed ransomware and is considered by many security experts the next step in the evolution of scareware.
Such is the case with a new version of “Total Security 2009," a notorious fake antivirus program. “Once the computer becomes infected, Total Security forces the victim to purchase it before it will allow any files from being accessed on the system," Sean-Paul Correll, threat surveillance specialist at Panda, warns.
Attempting to open any application on the compromised machine will result in a fake security alert being displayed in the system tray. "WARNING! Application cannot be executed. The file [name.ext] is infected. Please activate your antivirus software," the rogue notification reads.
The inability to use the infected computers has a good chance of convincing its owners to pay $79,95 for a license code. However, that would clearly be a mistake, as security researchers have cracked the ransomware and released valid serial numbers that can be used to unlock the systems. Here are a few of them, courtesy of Panda Security:
WNDS-TGN15-RFF29-AASDJ-ASD65
WNDS-U94KO-LF4G4-1V8S1-2CRFE
WNDS-6W954-FX65B-41VDF-8G4JI
WNDS-G84H6-S854F-79ZA8-W4ERS
WNDS-TTUYJ-7UO54-G561H-J1D6F.
Please note that simply using them will not remove the infection. It will, however, make it possible to install a legit and capable antivirus program and perform a scan with it.

 14 DAY TRIAL //
14 DAY TRIAL //