Security researchers warn that a new malware distribution campaign uses fake versions of the malicious site warnings commonly displayed by Firefox and Google Chrome.
Both Chrome and Firefox tap into Google's Safe Browsing service in order to check if the accessed URLs are known attack sites.
If such malicious pages are detected, both browsers block them and display warning messages.
In such circumstances users are normally given the option to either leave the site or override the block and continue to load the page.
Even if Google's blacklist-based approach does not provide the same level of protection as an antivirus product's real-time Web shield, it is still better than nothing and a good way to limit long time exposure to attacks.
Security researchers from F-Secure now warn that malware pushers are increasingly abusing the trust users associate with these browser warnings, in order to infect them.
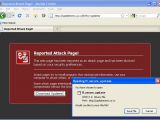
Malicious websites that mimic both Firefox's "Reported Attack Page" alert, as well as Chrome's "this site may harm your computer" warning, have been spotted.
The pages look exactly the same as the real thing, except for a button that reads "Download Updates," suggesting that security patches are available for the browsers.
The executable files served when these buttons are pressed install rogue antivirus programs, which try to scare users into paying a license fee.
This method of abusing browser warnings is relatively new, but has been documented before. A similar trick involves fake Firefox "What's New" pages.
However, the users who land on these latest sites discovered by F-Secure are also exposed to drive-by downloads via a hidden IFrame, which loads the Phoenix exploit kit.
Such attacks target vulnerabilities in outdated versions of popular software like Java, Flash Player, Adobe Reader or even the browsers themselves.
Successful exploitation results in malware being installed on the target computer in a way that is completely transparent to the victim.
Users are advised to keep their antivirus programs up to date and if possible to use script-blocking technologies available to their browsers, such as the NoScript extension for Firefox.

 14 DAY TRIAL //
14 DAY TRIAL //