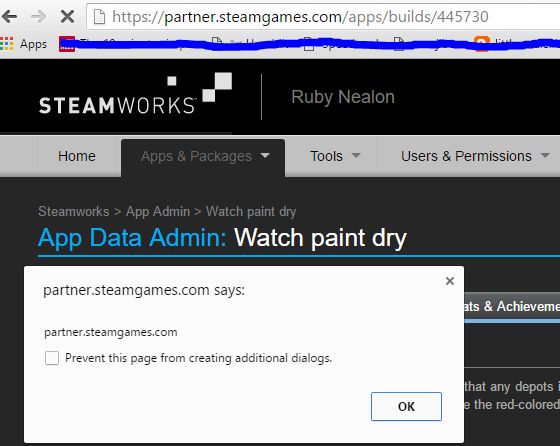
The 16-year-old security researcher who two days ago uploaded a game on Steam called "Watch Paint Dry" without Valve admins having a clue about it, is now back with two new bugs, an XSS and a CSRF, affecting Valve's Steamworks game developer panel.
After his prank made headlines on most major news media outlets in the past two days, Valve's team decided not to hold a grudge against the researcher and continue to allow him access to the backend panel destined only for game developers, known as Steamworks.
The researcher, Ruby Nealon, a teenager from the UK, didn't wait for a second invitation, got down to work, and managed to discover two new issues in the same panel he had abused before. This time around, instead of bypassing Valve's admins, he discovered a way to become one.
XSS in Valve's SteamDepot feature
In a technical write-up on his Medium blog, Nealon explains that the XSS (cross-site scripting) issue affected SteamDepot, which is Steam’s internal system for holding game content. SteamDepot is practically a repository for game builds (versions), and these versions are generated using scripts and a command-line based Steam client.
The researcher discovered that he could add JavaScript code in these scripts, which he did, inside the description field. Once the Steam script is executed and a new game build generated, it will appear in each game developer's profile, along with the malicious JavaScript code.
To highlight the danger of his bug, Nealon created a script that would steal anyone's Steam cookies and send them to his own server, if they accessed his Steamworks page where the compromised build would be displayed.
Steamworks featured minimal anti-CSRF protection
If an attacker manages to ask and trick a Valve admin into reviewing their build, the malicious script would execute when the admin would access the game developer's profile, and send their cookie to the attacker's server.
This cookie contains the admin's session ID, which, thanks to a lack of proper anti-CSRF (cross-site request forgery) protection for the Steamworks backend panel, would allow the attacker to forge browser sessions and pass as a Valve admin. This means that the attacker would have access to controls to publish games, which in a worst-case scenario could be altered to contain malware.
Nealon told Steam about their problems, and all issues were fixed yesterday, less than two days after they were reported. Despite his tremendous works in the past week, Nealon has decided to stop searching for bugs on Steam, since Valve doesn't run a professional bug bounty program that would reward him for all his time spent hunting for bugs and exploits.
 14 DAY TRIAL //
14 DAY TRIAL //