Attackers have used malware that specifically targets Linux machines to build an immense DDoS botnet capable of launching attacks of 150 Gbps and higher, as Akamai Security Intelligence Response Team (SIRT) reports.
The botnet revolves around the XOR trojan, a malware first observed in the wild in September 2014 by the Malware Must Die group. The botnet is different from other similar tools because it targets computers running Linux, instead of Windows, as most DDoS botnets do.
As Akamai reports, there's a campaign going on right now that utilizes XOR-infected Linux machines to launch DDoS attacks on the gaming sector and against educational institutes.
XOR DDoS botnet is currently active only in Asia
Akamai also reports that the first attack was seen on August 22, and up to 20 different targets are attacked on a daily basis.
90% of the DDoS targets are in China, the same country XOR's creators are rumored to be from. This is supported by the fact that the IP addresses of all C&C servers are also located in Asia, where most of the infected machines also reside.
Akamai's researchers did not observe an evolution in the malware's code, XOR still using brute-force attacks to acquire SSH login credentials and gain access to targeted machines.
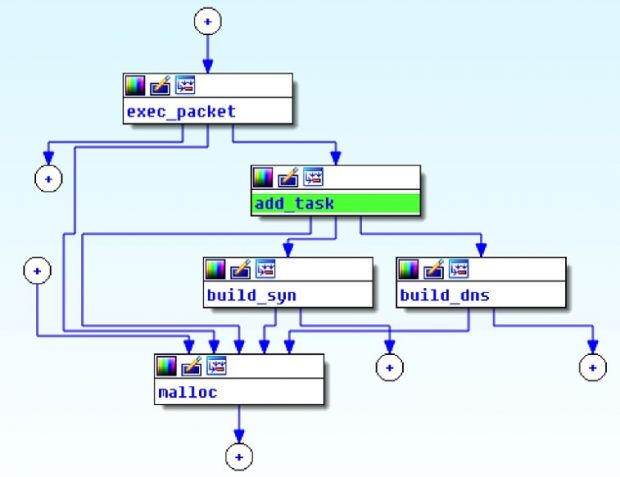
After this happens, attackers will run a simple shell script which downloads the XOR trojan, loads appropriate modules based on the local Linux machine configuration, and installs a rootkit to remain in control of the infected system. Avast's security team was the first to analyze this malware, and you'll find a detailed description of the malware's MO on their site.
Akamai provides a four-step guide to remove the XOR DDoS trojan
Additionally, Akamai's SIRT team has also analyzed the recent version of the XOR malware, and you can read their research as well.
The Akamai report also includes details about the four steps Linux administrators need to take to remove the XOR infection from their machine.
If you have annoying Linux friends that like to brag about how Linux has no viruses, this might be the perfect time to mention XOR, along with the Spike DDoS toolkit, and the IptabLes and IptabLex malware.

 14 DAY TRIAL //
14 DAY TRIAL //