Malicious Flash updaters have always been around packing malware droppers which would install a wide range of malware, but Palo Alto's Unit 42 got wind of an unusual fake Flash updater which will also update Flash to the latest version besides adding the XMRig crypto miner on the victim's system.
This new fake Flash updater strain displays legitimate pop-up notifications from the official Adobe installer and has been observed in the wild as early as August 2018.
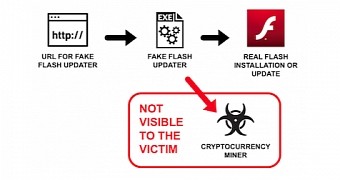
This malware campaign uses URLs controlled by the attackers which spread the fake Flash updater installers, which once launched on the victim's system it will display an accurate looking Flash updating screen.
While the fake Flash installer will update the target's Flash installation, it will also install the XMRig cryptocurrency miner in the background.
The fake updater will actually download a Flash installer from Adobe's updates website drawing the victim's attention from the crypto miner which connects to the xmr-eu1.nanopool.org mining pool and will start working, mining for Monero coins and drawing 100% of all CPU resources.
The XMRig crypto miner will be installed in the background while the foreground process will update Flash using installers downloaded from Adobe's servers
"While searching for these particular fake Flash updates, we noticed Windows executables file names starting with AdobeFlashPlayer__ from non-Adobe, cloud-based web servers. These downloads always contained the string flashplayer_down.php?clickid= in the URL," said security researcher Brad Duncan.
Unit 42 was able to uncover 113 malware samples that were using these URLs since March 2018, with 473 different file names used for the fake Flash updaters peddling this XMRig Monero miner.
What's interesting about these fake Flash updaters is that the actor behind them decided to put the extra work in to make them look as legitimate as possible, going to the length of actually adding Flash updating capabilities.
Duncan also said that "This campaign uses legitimate activity to hide distribution of cryptocurrency miners and other unwanted programs. Organizations with decent web filtering and educated users have a much lower risk of infection by these fake updates."
 14 DAY TRIAL //
14 DAY TRIAL //