A new campaign that uses compromised WordPress sites to redirect users to websites hosting Flash exploits was spotted in the wild by Internet security company Zscaler.
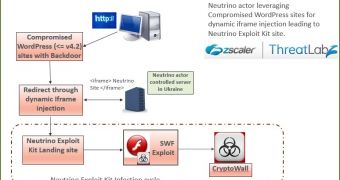
This new campaign seems to be utilizing the Neutrino Exploit Kit and uses a combination of hacked WordPress sites, hidden iframes, Internet Explorer, a Hacking Team Flash exploit, and the CryptoWall ransomware.
A complicated, yet effective infection cycle
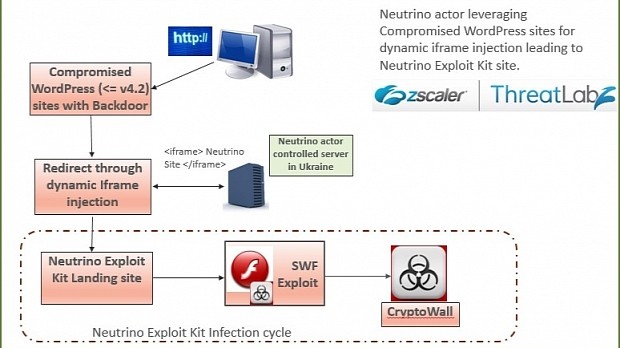
As Zscaler researchers are explaining, the starting point of this new campaign resides with over 2,600 hacked WordPress sites, to which attackers have gained login credentials, infecting over 4,200 pages with a hidden iframe that silently redirects users to malware-infected landing pages.
As a common pattern, all hacked WordPress sites seem to be running a version of the CMS of 4.2 and prior.
On these landing pages, a single Flash SWF file is served, but only to Internet Explorer users and only once, file which leverages the CVE-2015-5119 Flash zero-day exploit to infect the user's PC with a CryptoWall ransomware.
The campaign is undetected by most antivirus vendors
Zscaler researchers noted that the initial Neutrino Flash SWF file contains a secondary SWF, which is eventually used to deliver the malware payload.
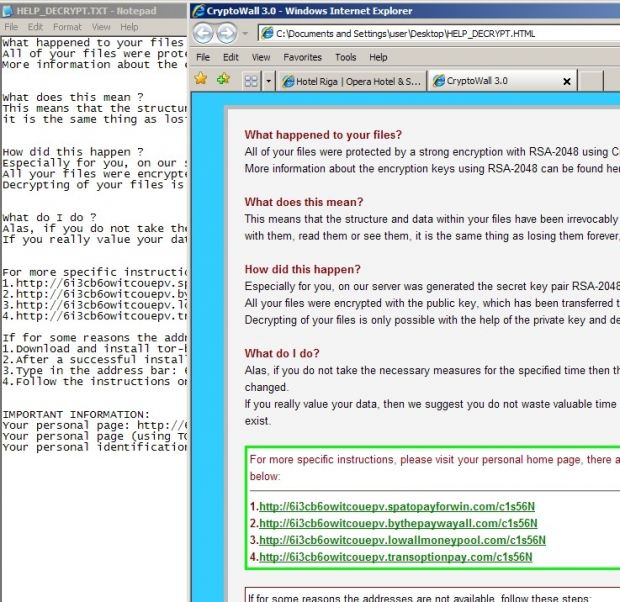
This latter SWF file delivers an encrypted executable file, which installs a version of the CryptoWall 3.0 malware, effectively locking the user out of his own files.
Only one AV vendor was able to detect the first SWF file as malicious, while the second SWF file triggered alarm bells for only two vendors, different from the first.
Since detection is quite low for this newer version of the Neutrino Exploit Kit and CryptoWall ransomware is near impossible to remove without paying the ransom, we recommend dropping Internet Explorer as soon as possible.
 14 DAY TRIAL //
14 DAY TRIAL //