Automattic, the company that supervises WordPress and WooCommerce development, has patched a persistent XSS (cross-site scripting) vulnerability in the WooCommerce e-commerce plugin for WordPress.
This bugfix is crucial because it has the potential to affect over one million WordPress-powered stores, according to the most recent statistics from the WP Plugin Directory.
Cengiz Han Sahin, security researcher for Securify, a Dutch security company, has discovered the vulnerability as part of the Summer of Pwnage event, which is taking place in Amsterdam during the month of July.
Summer of Pwnage is a unique event that gathers security researchers from around the globe, and this year, they have set their sights on discovering and reporting security bugs in the WordPress platform.
Malicious images deliver the XSS payload
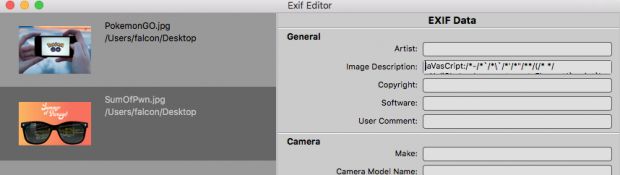
According to a technical explanation, the vulnerability resides in the fact that WooCoomerce pulls metadata from uploaded images and uses it as the title and description fields showed as captions near images on the store's frontend.
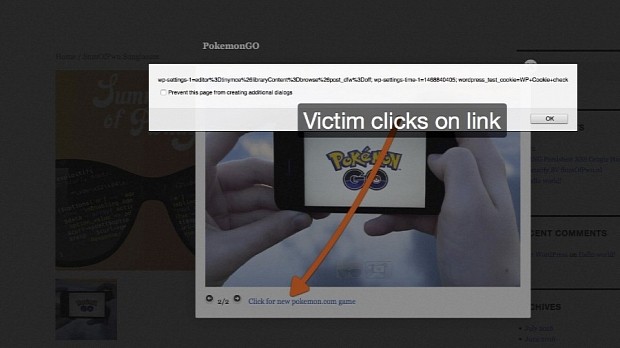
Since anyone is free to edit a picture's metadata, an attacker only has to enter an XSS payload in the metadata fields and social-engineer their way into tricking a store admin into using the malicious image for their product's main image or as part of the product image gallery.
When WooCommerce displays the image, either in the backend store admin panel or on the site, the malicious payload executes and carries out the desired attack.
Since XSS issues are the perfect entryways for launching all sorts of attacks on online applications, an attacker only needs the appropriate payload to steal cookies or CSRF tokens in order to take over admin accounts and indirectly the site.
Sahin said that they only tested WooCommerce version 2.6.2 against this vulnerability and that the WooCommerce team put out version 2.6.3 to fix the problem.
WordPress is not affected, despite the presence of a similar function
Because WordPress also uses metadata content to fill in image titles and descriptions for the pictures uploaded and embedded on your site, Softpedia has reached out to the researcher and inquired if the WordPress core needs patching as well.
"They [WordPress core devs] use the same type of sanitization but Woo introduces the XSS bug by performing double encoding," Sahin has told Softpedia today.
Summer of Pwnage is not over, so stay tuned for more security bugs. Previously, security engineers part of this same event discovered a similar persistent XSS issue in today's most popular WordPress plugin, All in One SEO.
Below is a picture showing how an attacker could edit an image's metadata to add their malicious payload.
 14 DAY TRIAL //
14 DAY TRIAL //