Security researchers Matt Nelson and Matt Graeber have discovered a unique method of bypassing the Windows User Access Control (UAC) security system on Windows 10 and allowing malicious files to execute without alerting users that something strange happened.
Their method doesn't involve a complicated mechanism that implies a privileged file copy or any code injection, but only taking advantage of an already existing Windows scheduled task that's set up to run with the highest privileges available.
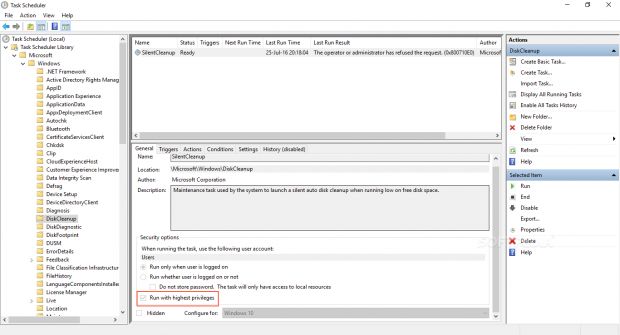
That scheduled task is associated with the Disk Cleanup utility, a built-in Windows app for helping users clean and manage their hard drives. The scheduled task is described as: "Maintenance task used by the system to launch a silent auto disk cleanup when running low on free disk space."
UAC bypass uses basic DLL hijacking technique
The two researchers discovered that, when Windows 10 ran this task, it would execute the Disk Cleanup app, which would copy a set of files in a folder at "C:/Users/AppData/Local/Temp."
The files copied here were an executable called DismHost.exe and a very large number of DLL files. Disk Cleanup would then execute the EXE file, which it would load one DLL after the other.
The two researchers discovered that DismHost.exe would load the LogProvider.dll as the last DLL file in this queue, giving them time to launch an attack.
Nelson and Graeber created a malicious script (aka malware) that would watch the local file system for the creation of new folders inside the Temp directory, and when detecting one of the files above, it would quickly move to replace LogProvider.dll with their own version of the DLL, containing malicious operations.
UAC would ignore the scheduled task
This attack technique is called DLL hijacking and is a common method of executing malware attacks.
Because this scheduled task ran from a regular user account, but with the "highest privileges available," UAC remained silent.
An attacker clever enough to use this technique would have had a way to infect a regular user account and then execute code with admin privileges with a very trivial DLL hijacking technique.
A fix ain't coming
The good news is that the researchers have told Microsoft about the issue. The bad news is that a fix isn't coming in the immediate future.
"This was disclosed to Microsoft Security Response Center (MSRC) on 07/20/2016," Nelson writes. "As expected, they responded by noting that UAC isn’t a security boundary, so this doesn’t classify as a security vulnerability."
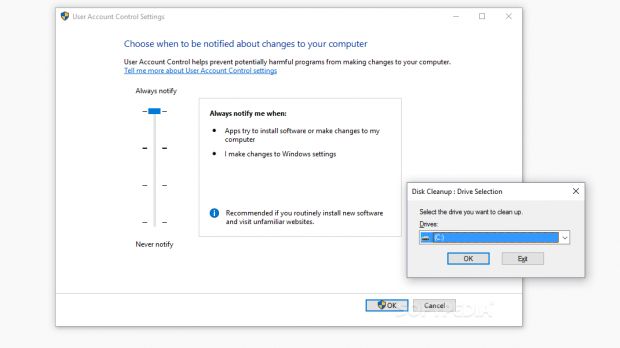
In the meantime, users are encouraged either to disable the task or to uncheck the "Run with the highest privileges" option as seen below.
To get to this window, press the Start button, and search for "Schedule Tasks." Open the application, and on the left side of the window, open the following folders: Microsoft -> Windows -> DiskCleanup. Here use the menu on the right side to disable the task, or just untick the problematic box.
UPDATE [July 27, 2016]: Two days before Nelson and Graeber published their proof of concept Windows 10 UAC bypass, German security researcher Stefan Kanthak also disclosed a similar issue.
This issue also involved DISM.exe copying files in the Windows Temp folder and opening the door for DLL hijacking attacks. It also affected Windows 7, 8, and 8.1 users.
Kanthak said in his report that most vulnerable are users employing the default account created during Windows' installation. According to Microsoft data, these are almost half of Windows 7-10 users.
Microsoft has declined to fix this issue as well, calling it "by design." Kanthak offered some mitigation options.
 14 DAY TRIAL //
14 DAY TRIAL //