Malvertising campaigns during the past year have grown in sophistication, adding support for a new technique called "fingerprinting" that identifies victims at the ad level, or before they hit the final website, where the exploit kit infects them with malware.
Malvertising is the practice of disguising malicious code inside an ad which is delivered through a trusted ad platform on legitimate sites. While in the beginning malvertising campaigns were easy to spot, as the criminals behind them gained more experience, their coding skills advanced as well.
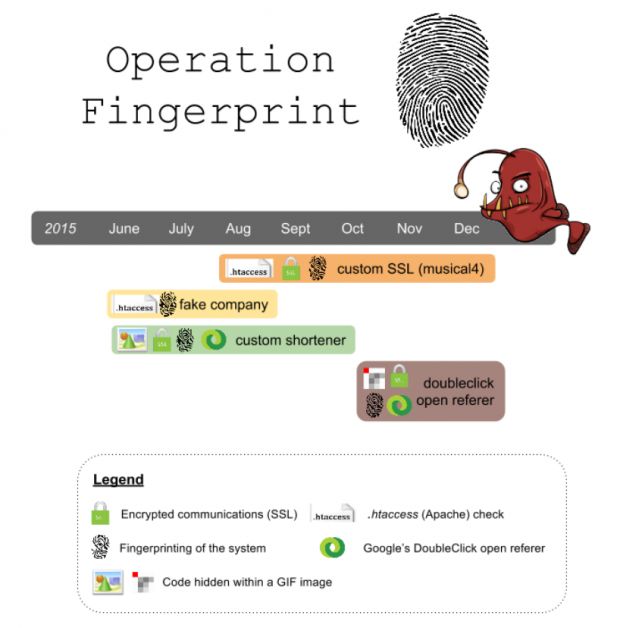
The latest addition to their arsenal of nefarious tricks is the Fingerprint technique which was created to separate malvertising victims for the purpose of optimizing malware delivery only to the potential users that can be infected.
The Fingerprint technique
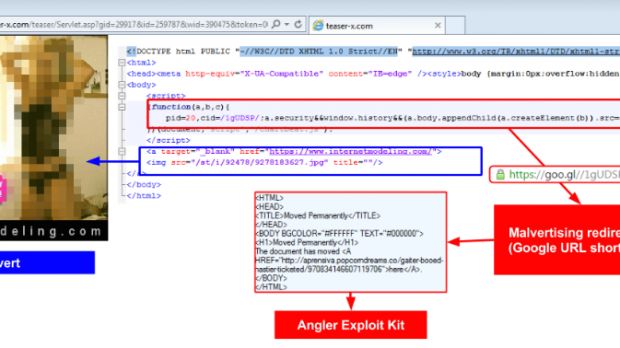
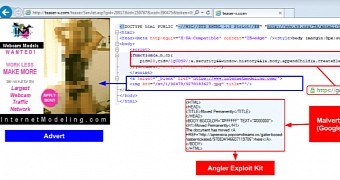
Malvertising works by executing malicious code, even without the user's interaction, and automatically redirecting users through a series of intermediary sites (called gates), and then sending them to a "landing page" where an exploit kit leverages vulnerabilities in the user's PC to deliver malware.
The Fingerprint technique uses filters, added to the intermediary points (gates), or even at the ad level, which separate users.
First it separates researchers from legitimate victims. This is done by exploiting a vulnerability in Internet Explorer’s XMLDOM ActiveX control (CVE-2013-7331), which allows attackers to see local pathnames.
By checking for the presence of an antivirus or traffic debug software, malvertisers can avoid "risky" users that might be researchers or users with strong security software that might alert cyber-security vendors of a malvertising campaign. Additionally, this first filter is also how malvertisers detect honeypot test servers set up by ad networks to detect malicious ads.
Once they manage to evade the "risky" users, malvertisers use the Fingerprint technique to filter the victims, either based on their IP, browser type, OS version, or some other condition based on the vulnerabilities ready to be deployed via the exploit kit.
The Fingerprint technique makes malvertising more efficient, harder to detect
The technique was widely used last year in malvertising campaigns that affected millions of users. Besides fingerprinting, these malvertising campaigns also shared other similarities.
These included the usage of goo.gl URLs in the malicious redirections, using the Angler exploit kit for the landing page, the usage of fake advertiser domains belonging to non-existent companies, and the use of SSL for hiding the malicious traffic from both security vendors and ad networks.
To further avoid detection, these malvertising campaigns also executed their fingerprinting code only once, to avoid repeat.
The malvertising campaigns were mainly targeted at residential IP addresses, mostly affected users living in the US, Canada, or Great Britain, and cost the criminal group no more than 19 cents per 1,000 ad impressions.
Fingerprinting played a crucial role in keeping malvertisers ahead of security researchers, and as it stands today, malvertising is the biggest security threat to Internet users, not the FBI decrypting that darn San Bernardino iPhone.
For more details, we recommend checking out Malwarebytes and GeoEdge's Operation Fingerprint report.
 14 DAY TRIAL //
14 DAY TRIAL //