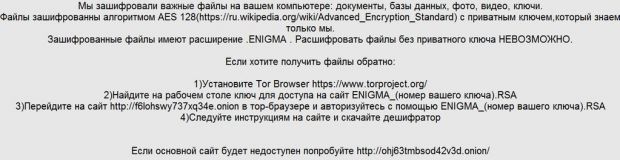
AVG security researcher Jakub Kroustek has discovered a new ransomware that's targeting only Russian-speaking users named Enigma, which, under certain conditions, can allow users to recover some of their files using Shadow Volume Copies.
Analyzed by researchers from MalwareHunterTeam and Bleeping Computer, the ransomware encrypts files with the now de-facto AES-RSA dual encryption model and then stores the encryption key on the computer's Desktop in the form of a file named ENIGMA_[NUMBER].RSA.
If users want the decryption key, they'll have to pay crooks 0.4291 Bitcoin, which is about $200. As with other ransomware families, payment must be made by accessing a browser on the TOR network, via the Tor Browser. On the payment site, they'll be asked to upload the file mentioned above.
Enigma ransomware uses HTML files to deliver its payload
The ransomware's current distribution model is via simple HTML files. In recent months, security researchers have seen an invasion of ransomware families that install themselves via JavaScript code. Such is the case with Enigma. When users open the HTML file, the malicious code contained inside it executes and offers another JavaScript file for download.
Users who launch this JavaScript file into execution will start another malicious operation that builds an EXE file on the local computer and then launches that EXE into execution as well. This executable is the Enigma ransomware, which immediately starts encrypting files. Once it's done, it creates and executes an HTA file, which is the ransom note. This file is also set to start with the OS.
A small chance of recovering your files
As for the possibility to decrypt files, this is a simplified explanation of what happens towards the end of the encryption process that you need to remember just in case you double-clicked an HTA file.
Apparently, for users that have Windows UAC (User Account Control) enabled, the ransomware will show a UAC prompt at one point towards the end of the encryption process.
If users press "No" in this prompt, the ransomware's encryption routine ends without deleting the Shadow Volume Copies. The files will remain encrypted though, and you'll be able to spot them based on their ".enigma" file extension. To recover your files, there's specialized hard drive recovery software that can extract data from Shadow Volume Copies.
So today's lesson is that we need to leave Windows UAC turned on, something which security researchers have been saying for years. As said before, the ransomware only targets Russian users. For now!

 14 DAY TRIAL //
14 DAY TRIAL //