Dubbed an "accidental hero," a cybersecurity researcher tweeting under the MalwareTech handle has managed to find a kill switch to stop the spread of the WannaCry ransomware.
Working together with Darien Huss from Proofpoint security firm, the researcher managed to dig into the WannaCry code and found a kill switch. Hardcoded into the malware in case the creator wanted to stop it from spreading there was a nonsensical domain name that the malware made a request to. If the request was successful, the kill switch went into effect and the malware stopped spreading.
All it took MalwareTech to do was to register that domain since the attackers didn't bother to do it. They say they didn't even realize that this would put an end to the propagation of the malware until after the deed was done. The problem now is that the attackers can, at any point, fiddle with the code and take out the kill switch altogether or change it to a domain they have registered. Since site domain registration is trackable, however, that may not happen, leaving the first option as the most viable one.
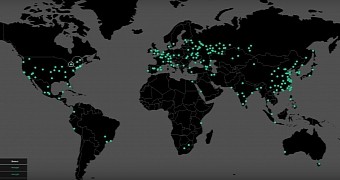
Up until now, Bitdefender said they've noticed some 180,000 infected devices. Out of all these victims, only 102 decided to pay the $300 worth of Bitcoin ransom, totaling about $27,000 for the attackers, according to Troy Hunt. The malware spread in 104 countries before being stopped, including the United Kingdom (where it blocked the NHS network), Russia, Ukraine, China, India, Italy, Egypt, and so on. The United States has seen fewer infections, in part thanks to the discovery of the kill switch.
What is WannaCry?
Ransomware as a whole has become increasingly popular, being the go-to weapon for most cybercriminals looking to make a quick buck. WannaCry is a special kind of ransomware as it exploits a vulnerability called MS17-010 that is present in most versions of Windows.
The flaw became visible to everyone after a hacker group called Shadow Brokers dumped a series of NSA files online, detailing EternalBlue, a zero-day exploit.
WannaCry is a hybrid threat combining a ransomware payload with a wormable behavior, which makes it the most dangerous piece of ransomware written until now.
There are several ways to protect yourself from an attack. One of them is to run an updated version of Windows. Microsoft has already released a patch to protect users of this zero-day attack, but it seems that not everyone applied the update.
The company went as far as to release a patch for Windows XP, even though the operating system has been discontinued and should no longer receive any security updates. Windows XP, Windows 8, and Windows Server 2003 users can download the patch from the Microsoft Update Catalog.
The other way to stay safe is to install a security software to keep your device protected. At this point, most of them should have included WannaCry in their libraries.
 14 DAY TRIAL //
14 DAY TRIAL //