A vulnerability that allowed abuse by attackers was discovered and quickly fixed in the Kaspersky Internet Security antivirus package, one which allowed hackers to spoof traffic and use the antivirus product against the user and itself.
Google Project Zero security researcher Tavis Ormandy is on a roll these days, finding zero-day exploits in the same Kaspersky antivirus in early September, and then another one in the Avast antivirus just the past week.
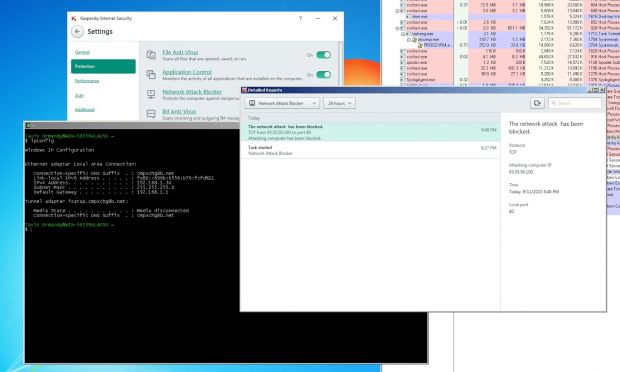
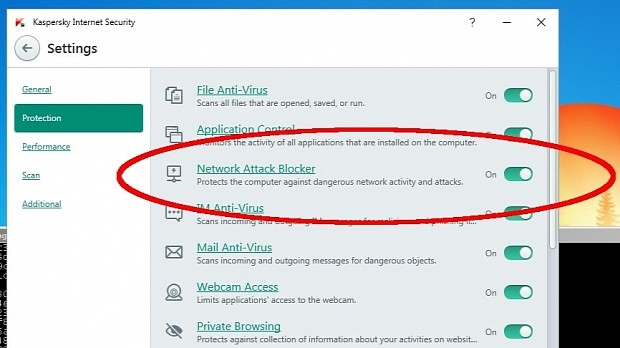
Now he turned his sight to the Kaspersky Internet Security package, more specifically to its Network Attack Blocker component, a feature which protects computers against malware and other attacks that rely on the Internet or a local network to propagate.
According to Mr. Ormandy's research, the problem is actually a design flaw, the Network Attack Blocker being "a simple stateless packet filter with a pattern-matching signature system."
This means that the component scans each network packet in turn and does not keep track if the stream from which it originates has been already cleared before.
The antivirus could have been used to block Windows Update
If a malicious packet is detected trying to slip in, the Kaspersky antivirus simply blacklists that packet's origin IP address.
As Mr. Ormandy explains, an attacker could easily spoof a network packet, and then fool the antivirus in blocking services like Windows Update, Kaspersky's own update servers, or any other IPs which might cripple a computer's defenses, allowing it to carry out further attacks later on.
Additionally, because the Network Attack Blocker does not understand context (application layer), the antivirus can also be fooled into blocking IP addresses by simplify embedding a virus signature into an image's metadata, or inside an email.
The vulnerability was detected and reported to Kaspersky on September 11, and the security vendor issued a fix on October 8.
UPDATE: Softpedia has contacted Kaspersky over the issue, to which the company responded:
"Kaspersky Lab has corrected the conditions for blocking IP addresses by the Network Attack Blocker component of our products that could have led to prohibiting access to legitimate network resources.
"Our specialists have seen no evidence that this particular flaw has ever been exploited in the wild.
"The fix for this software flaw was delivered to all Kaspersky Lab products that offer the Network Attack
"Blocker functionality, via automatically updated modules on October 6, 2015. To learn more, please visit our Technical Support page.
"We would like to thank Mr. Tavis Ormandy for reporting this vulnerability to us in a responsible manner. We greatly appreciate his effort and his findings, which were backed by the computing power of Google Project Zero."
 14 DAY TRIAL //
14 DAY TRIAL //