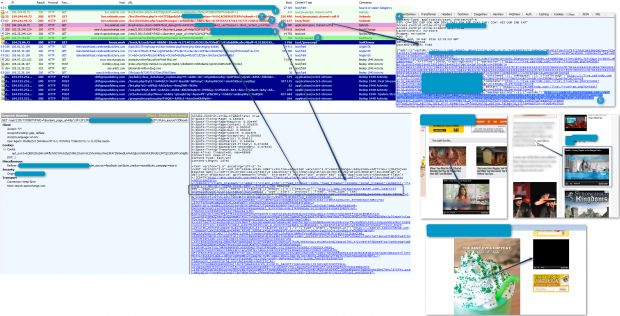
A malvertising campaign that affected high-profile sites, first detected on March 13, has now evolved and is showing malicious ads on top of videos, not only in banners and static ads.
In its early stages, the malvertising campaign was spotted via static ads on sites such as Microsoft's MSN portal, the New York Times, the BBC, AOL, Comcast's Xfinity, NFL, Realtor, the Weather Network, The Hill, and Newsweek. Later, malicious adverts were also found on CBS Sports, LA Times, New York Post, The Guardian, and the Toshiba and Lenovo homepages.
The malicious ads were delivered via the Google, AOL, Rubicon, and AppNexus platforms, and were redirecting users to the Angler exploit kit, which infected them with the Bedep malware, a well-known clickfraud bot.
Two weeks later, attackers shift to video-based malvertising
Three security firms that confirmed the first wave of malvertising attacks are Trend Micro, Trustwave, and Malwarebytes. Now, almost two weeks later, Proofpoint is providing new information about how the campaign evolved after most of the world's attention moved back to the FBI vs. Apple catfight.
It appears that after most of the initial points of infection were brought down by the affected advertising platforms, the group behind this attack (named SadClowns) has changed tactic and started delivering malicious code via video ads.
Video malvertising is not new, but this campaign has a novelty factor
While video-based advertising has been observed in the past, most notably during a two-month-long campaign last November, Proofpoint says that this is the first recorded instance where video malvertising has redirected users to exploit kits.
In the past, crooks leveraged Flash, XML and the VPAID advertising model to boost SEO scores for desired websites. On the other hand, using exploit kits like Angler automates the process of infecting users with malware, allowing malvertisers to gain a much higher profit from their work.
According to Proofpoint, this latest video malvertising campaign was spotted on sites such as DailyMotion, Photobucket, Gazeta.pl, and Whitepages.com. Later, in a second campaign, the malicious ads showed up in videos on Business Insider, FOX News, Wowhead, and other smaller websites.
SadClowns was redirecting video viewers, using video ads displayed via the SpotX (formerly SpotXchange) platform, to the Angler exploit kit. Angler would then deliver the final payload, which was the Evotob malware dropper and a Reactorbot banking trojan.
Because the previous malvertising campaign had made some headlines around the Internet, SpotX was quick to respond to Proofpoint's request, and the campaign was shut down in less than a day.
The group responsible for these campaign is very experienced. In the past, SadClowns had also delivered malicious ads on adult video platforms such as xHamster, PornHub, and YouPorn.

 14 DAY TRIAL //
14 DAY TRIAL //