The developers of popular forum software vBulletin are currently working on releasing a fix for an SQL injection vulnerability discovered by members of the largest hacking community in Romania, Romanian Security Team (RST).
The hackers discovered the glitch during routine security tests on their forum, which runs version 5.1.2 of vBulletin.
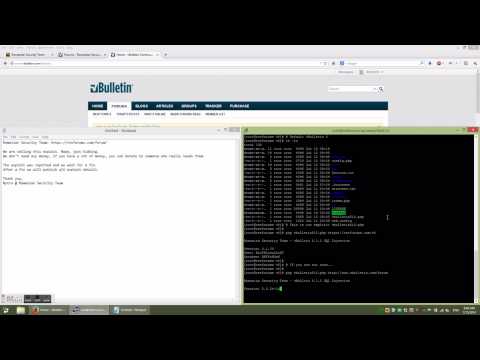
Nytro, one of the hackers involved in the testing process, told us via email that they found an SQL syntax error message and discovered the troublesome query upon closer examination, with the forum software installed in debug mode.
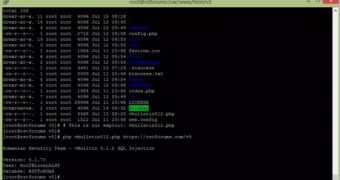
He says that the SQL injection is far from being complex, one of the queries not being properly sanitized. This offered the possibility to inject an SQL command, which allowed reading and extracting the details of all the admins without authorization.
Armed with this information, a potential attacker could gain access to the administration panel and from there, to databases containing sensitive information (usernames, email addresses, passwords); they could even execute code by writing malicious PHP code, if write permission is enabled.
Although SQL injection attacks are among the most trivial and widespread, exploits such as this one are worth a lot to cybercriminals, who can use this attack vector to gain access to sensitive information.
On underground forums, a zero-day exploit could be sold for thousands of dollars. However, Nytro told us that Romanian Security Team would not sell their finding. Instead, they disclosed it privately to vBulletin and will publish all the details as soon as a fix is released and is adopted by a larger crowd.
They are not at their first disclosure of a vBulletin vulnerability. Back in April, this year, Romanian Security Team made a responsible disclosure of several cross-site scripting (XSS) flaws that allowed a potential attacker to insert arbitrary web script or HTML to various sections in the vBulletin forum. The set of vulnerabilities was identified as CVE-2014-3135.
There are tens of thousands of websites relying on vBulletin for the forum section, and according to W3Techs, the software is one of the top choices for high-traffic websites. Not all the forums rely on version 5.x, though, which would limit the impact of the exploit.
vBulletin is a proprietary cross-platform software written in PHP, and a new version is in development at the moment.
 14 DAY TRIAL //
14 DAY TRIAL //