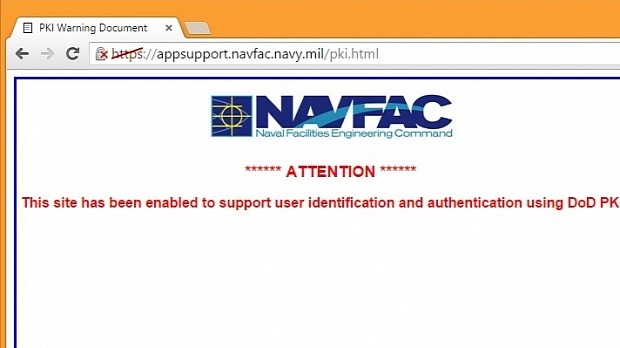
Despite the fact that the US is controlling one of the most active and sophisticated spying and hacking programs around, its official .mil websites are running over woefully insecure connections.
The revelation comes via Netcraft, which analyzed a series of military sites and found a vast majority deploying the old SHA-1 signed security certificates.
At the start of 2014, the US National Institute of Standards & Technology (NIST) banned CAs (Certificate Authorities) from issuing new SHA-1 signed certificates, a ruling that most CAs followed closely.
With a recent research study putting the cost of breaking SHA-1 encrypted connections at a sum between $75,000 and $120,000 (€67,000 and €107,000), the US military may need to look into the fact that its Department of Defense is still issuing quite a lot of these SHA-1 certificates.
The situation gets bleaker because these certificates weren't released before February 2014, when NIST banned this practice, but some of them were issued as recently as February 2015.
If you think that the US military webmasters may know what they're doing, then you're overestimating their skills since almost all major companies have slowly started moving away from SHA-1.
Just last week, alerted by the recent cracking of SHA-1, Mozilla decided to hurry up its process of completely moving away from SHA-1.
Right now, despite the NIST ban and the aforementioned research, the Internet is not yet ready to move away from SHA-1 certificates, with over 1 million sites still deploying them in production-level applications.
 14 DAY TRIAL //
14 DAY TRIAL //