A joint effort from multiple infosec researchers has uncovered more details about a mysterious new malware variant that appeared during the past weeks.
Named DELoader because it was seen targeting only users in German-speaking (DE) countries such as Germany and Austria, the trojan is a malware dropper, also called a malware loader, because its sole purpose is to "drop/load" other malware families on infected systems.
The researchers who analyzed the trojan say DELoader infects victims via malicious JavaScript files packed inside ZIP files delivered via spam email.
DELoader's C&C server wasn't secured, so researchers took a peek
When analyzing this malware, researchers discovered its C&C server, the IP address to which DELoader connects and asks for new instructions or the download URLs of the malware it needs to download for the infection's second phase.
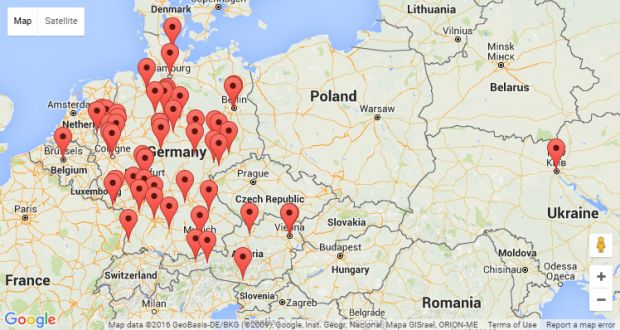
While looking at this C&C server, one researcher stumbled upon some open-access directories accessible via the Internet. Here, he found a log that contained the IP addresses of all targets infected with the DELoader malware.
Plotting all these IPs on a map, they discovered that, indeed, the trojan targeted only German-speaking users, because all the infections, except one, were located in Germany or Austria. The exception was an IP from Kiev, Ukraine. Malware coders often test their malware on their own systems, or in virtual machines.
Who is Alecksandr Sirofimov?
Creating a graph of all the server URLs from where crooks distributed DELoader, or the loader that connects to download the second-stage malware, researchers found something in common.
A large number of these domains were registered by a man named Alecksandr Sirofimov, who used the email address [email protected].
This was obviously a fake identity, but coincidentally or not, the details attached to the lone Ukrainian IP also included the name "Alexandr" in the PC's hostname.
Furthermore, the researchers found that some of the infrastructure used in DELoader's distribution was previously tied to another malware campaign that spread the Marcher Android malware, a dangerous mobile banking trojan.
DELoader has a long history in cyber-crime and malware distribution
"While DELoader is a relatively new malware, the findings in this research demonstrate that the threat actor behind it has actually been around for quite some time, and has left a substantial amount of fingerprints over the Internet," researchers noted.
"Historical information shows that the individual or group using the name 'Aleksandr' have been involved in bank information theft not only of German-speaking users, but have also targeted Australian users. It is possible that DELoader may be used to aid in similar purposes in the future."
The team of researchers who analyzed the malware includes security vendor Fortinet, French malware analyst Benkow, and JAMESWT from the MalwareHunterTeam. A researcher who goes by the nickname of Malware Must Die has reported that over 150 domains used in DELoader's campaign were or are in the process of being taken down.
#unknow https://t.co/DJhIkgsnoq @malwrhunterteam @F_kZ_ @benkow_ — JAMESWT (@JAMESWT_MHT) June 16, 2016

 14 DAY TRIAL //
14 DAY TRIAL //