UPDATE, December 28: The website has been taken down and is now flagged as "under construction," most likely as the admins are trying to patch the vulnerability and recover after the hack. Original story below.
The Turkish Chamber of Commerce and Industry in United Kingdom suffered a double hack the past days after two separate groups of hackers managed to breach their official website.
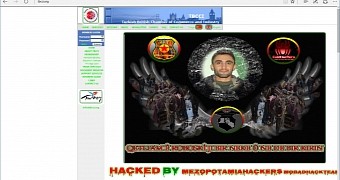
First and foremost, Kurdish hacktivist group Mezopotamia Hackers hacked the website and posted a message right on the main page in protest against what seems to be the Roboski massacre that took place in 2011 and which led to the death of 34 Kurdish villagers following an airstrike launched by Turkey.
While their motive is pretty clear, it’s not yet known if the Mezopotamia Hackers stole any information or compromised more than the index page to post the message that you can also see in the picture here.
Kapustkiy’s hack
In a separate hack, Kapustkiy, who has a good track on breaching chambers of commerce, also managed to compromise the site, this time with an attack that allowed him to access full names, emails, phones, and addresses of several individuals.
A database dump obtained by Softpedia seems to indeed include personal information for hundreds of people, such as names, addresses, and phone numbers. There’s also an administrator account whose password does not appear to be hashed.
Kapustkiy told us that he already contacted the site administrators, but no response was offered, so he decided to leak only part of the details to prove that he indeed got access to the database in question.
At the time of writing this article, the website still appears to be hacked and the message posted by Mezopotamia Hackers is still there, so there’s a good chance that the vulnerability exploited by Kapustkiy is also unpatched. This means that details of several hundreds of users are still exposed.
We’ve also tried contacting the site admins to report the breach and ask for more information, but no answer was received before publishing the article. We’ll update with more information as it is provided.
 14 DAY TRIAL //
14 DAY TRIAL //