A trojan that appeared at the start of the month on Russian underground hacking forums has now been integrated into the spam distribution chains used to deploy the Locky ransomware and Pony information stealer (infostealer).
The trojan, named Quant Loader, is sold to anyone interested and advertised as a new malware dropper that can be used as a first-stage infection, which can later stealthily download more advanced malware.
Quant Loader used to deliver Locky and Pony
According to a report from security firm Forcepoint, the new trojan appeared on September 1, and by September 12, it was already part of spam campaigns.
Currently, the people behind the Locky ransomware (Zepto variant) and the Pony campaigns have apparently purchased it and are now deploying it.
These spam emails come with ZIP files attached which, when decompressed, dump a Windows Script File (WSF) on the user's PC.
Running this file downloads Quant Loader which, after getting boot persistence, downloads Pony or Locky.
Quant Loader peddled on Russian hacking forums
According to its forum advertisement, the crooks claim this is a new trojan written from scratch, can download and install both EXE and DLL files, and escalate user privileges without any "aggressive" techniques.
Quant Loader also provides buyers with an admin panel that allows them to control what malware to push to infected PCs, and target computers by geographical location.
To avoid antivirus detection and to optimize malware installs, the Quant Loader crew says the trojan can limit the number of needed downloads, and optionally balance downloads across different servers.
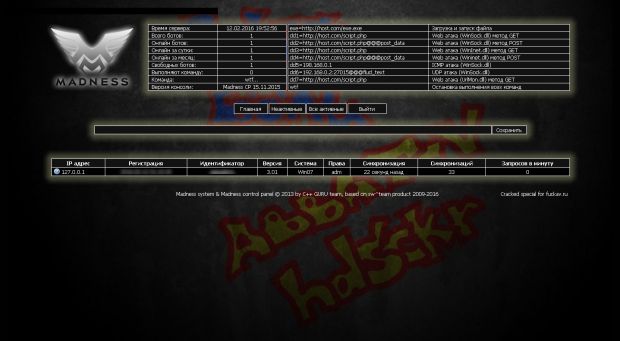
Quant Loader developed by CPPGURU squad, creators of Madness DDoS
A technical analysis by Forcepoint proves Quant's creator exaggerated. The trojan is not as new as he claims, and it appears he reused much of the codebase from the Madness DDoS trojan. In fact, some VirusTotal scans will label Quant Loader under terms used for Madness, such as "Pliskal" or "Crugup."
The security firm found evidence that these operations are linked. "MrRaiX" aka "DamRaiX," Quant Loader's seller is actually part of a bigger malware crew named "C++ GURU" aka "CPPGURU."
This group is also selling access to the Madness DDoS trojan that helps build a DDoS stresser service, the Z*Stealer information-stealing trojan, and the MBS Bitcoin-mining trojan.
The links are also evident through the "copyright" watermark on both Quant and Madness backend panels, which include the gang's name.

 14 DAY TRIAL //
14 DAY TRIAL //