The handlers of TorrentLocker file-encrypting ransomware started to move their operation from Australia and are currently sending fraudulent emails to users in Europe, those in the United Kingdom being the most targeted.
Historically, Australia was the country where most TorrentLocker attacks were recorded, but security researchers observed that spam campaigns delivering this piece of malware have decreased in the region.
Cybercriminals are now focusing their operation on countries like the UK (33.48%), Turkey (21.44%), the United States (14.60%), Italy (10.85%) and Germany (6.38%), according to telemetry data from Trend Micro. Other countries are also affected, with Spain and Poland also being on the list.
Same lure works in other countries
The method of compromise does not differ from what has been seen in Australia. The victim receives an email claiming to be from a utility company or a parcel delivery entity (courier, post), and is instructed to download a file of interest from a provided link.
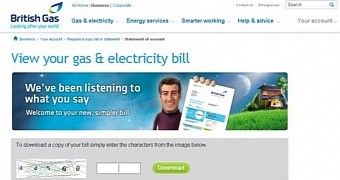
The URL leads to a spoofed website version of the organization and asks them to solve a captcha, for credibility. Once the file is downloaded and launched, the system is infected with TorrentLocker, which begins its file encryption routine. Trend Micro says that many of the victims are from the healthcare sector.
Emails distributed to users in the UK purport to be from British Gas or government bodies like the Home Office or the Ministry of Justice.
Some C&C have been used by Tinba
“A wide variety of sites are used in these attacks. About 800 compromised domains were used to host the images in the emails, or to serve as redirector sites for links within the emails. Meanwhile, the fake sites themselves are hosted on Russian and Turkish servers,” the researchers found during the analysis of the campaign.
It was observed that some of the IP addresses acting as command and control (C&C) servers were used in attacks with other pieces of malware, one of them being employed by Tinba banking Trojan.
Some of the C&C domains are hosted in Russia and France and were registered using a domain privacy service to hide details about the registrant.
 14 DAY TRIAL //
14 DAY TRIAL //