AirDroid is currently one of the top Android apps available in the Google Play Store, with official statistics claiming that it already recorded between 10 million and 50 million downloads.
But being very popular doesn’t necessarily mean that the app is also entirely secure, and AirDroid is pretty much the best example.
Security company Zimperium has discovered security flaws in AirDroid that expose user data to cyber attacks, including usernames and passwords that are stored on the phone. And what’s worse is that the developers of AirDroid are already aware of the bug, but they don’t seem to be too interested in fixing it.
The bug
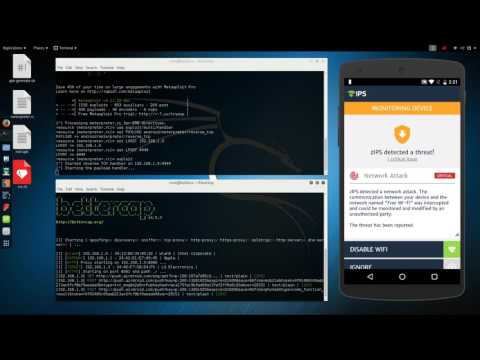
Specifically, Zimperium explains that AirDroid ships with several security issues that allow an attacker that uses the same network to launch a Man-in-the-Middle attack and intercept information transmitted by the app, including update requests.
This is possible because AirDroid uses insecure communication channels and requests are encrypted with DES (ECB mode), but the encryption key is hardcoded inside the app itself, as the security firm explains.
With an MITM attack, a cybercriminal could be able to deploy a malicious APK on any device running AirDroid and then get full access to the phone. This would, in turn, provide the attacker with quick access to other information stored on the device, including email address and passwords (credit card data can also be exposed if it’s stored locally).
“Our research highlights how insecure communication channels make millions of users vulnerable to Man-in-the-Middle (MITM) attacks, information leakage and remote hijacking of update APK which leads to a remote code execution by a malicious party. The attacker exploits the app’s built-in functionalities and uses them against its users,” Zimperium explains.
The patch
According to the security firm, the developing company was first informed about the bug on May 24, and 6 days later, they officially acknowledged the issue.
And yet, no patch was released since then, and what’s worse, AirDroid 4.0.0 and 4.0.1, which were launched on September 7 and November 28, respectively, are still vulnerable.
Zimperium decided to go ahead and publish the full disclosure on December 1, so users are still vulnerable to attacks, but it’s not yet known when a new and secure version of AirDroid would be launched.
How to protect against it
Unfortunately, this is not an easy task. Zimperium says that you need to either deploy dedicated software that can block such attacks or simply remove AirDroid until a fix is provided.
In most of the cases, such attacks are only possible when you are connected to free Wi-Fi networks, so if you avoid these hotspots, you should be secure as well. Of course, your own trusted network shouldn’t pose any threat.
 14 DAY TRIAL //
14 DAY TRIAL //