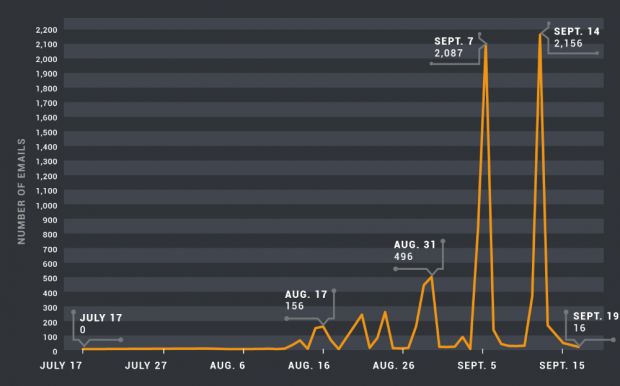
Cisco Talos says it detected out-of-the-ordinary activity from a botnet that has usually been very quiet for most of the past years.
Called Tofsee after the malware that helps control the bots, this botnet first appeared in 2013 when crooks first started infecting users.
For most of the time, the group behind it relied on malvertising campaigns to redirect users to malicious sites that hosted exploit kits and infected them with the Tofsee malware.
Tofsee and its historic relation with RIG EK
This particular threat transformed the user's PC into a bot used for clickfraud, cryptocurrency mining, and for sending spam. In most instances, the botnet was used to deliver pharma-related and adult dating "Russian bride"-like messages.
Cisco says that, for most of its lifespan, the Tofsee gang used the infrastructure of the RIG exploit kit to infect its victims with their malware.
As the exploit kit landscape changed this spring after the shutdown of the Nuclear exploit kit and the arrest of the crooks behind the Angler exploit kit, things also changed for Tofsee.
The RIG exploit kit operators had all of a sudden more clients to deal with, which meant less room to deliver the Tofsee malware. Nevertheless, the Tofsee-RIG partnership continued, mainly because RIG played second fiddle to the Neutrino exploit kit, which hoarded all the "big money" clients.
RIG moves on to bigger fish
Things changed this month, in September, when a highly publicized takedown of several malvertising campaigns relying on the Neutrino exploit kit sent a lot of clients to RIG operators.
As a direct result, less and less Tofsee malware was distributed via RIG, and the Tofsee gang had to find another way to spam their malware, in order to keep their botnet alive.
Botnets need to add new bots every day, as old ones are removed from infected PCs, or are blacklisted in spam lists. Because RIG gained a larger market share in the detriment of Neutrino, the Tofsee gang was forced to use their very own spam botnet to send spam with the Tofsee malware. The botnet reached a point where it was forced to devour itself to stay alive, risking the blacklisting of its own bots to generate new ones.
Tofsee resorts to spamming itself
When the Tofsee crew switched from pharma and adult dating spam to the delivery of emails with malicious attachments, Cisco Talos immediately picked up on the botnet's activity spike and irregular activity. The botnet had almost never spewed out emails with malicious Word files, which drew the security firm's interest, who is now keeping an eye on this new threat.
Spam overall is on a growing trend. Just a week earlier, another Cisco Talos report highlighted that spam was at all-time record levels since 2010, its glory days.
Spam botnets overall are now bigger than ever, and constantly growing. For example, in early August, the Kelihos botnet tripled in size in just 24 hours.

 14 DAY TRIAL //
14 DAY TRIAL //