WordPress site administrators should immediately check their sites for a new coordinated malware campaign that has infected thousands of sites in the last two days.
According to Sucuri, a company that provides website security solutions, hackers found a way to hijack websites and add malicious code to the site's JavaScript files.
When a user accesses the infected website, the JavaScript code is loaded into their browser, calling to a secondary backdoor hidden in the site's code, and finally forcing the user's browser to load an iframe.
This iframe calls to a remote Web page where the Nuclear Exploit Kit is hosted, scanning the user's browser, and identifying various entry points for the attacker's malware.
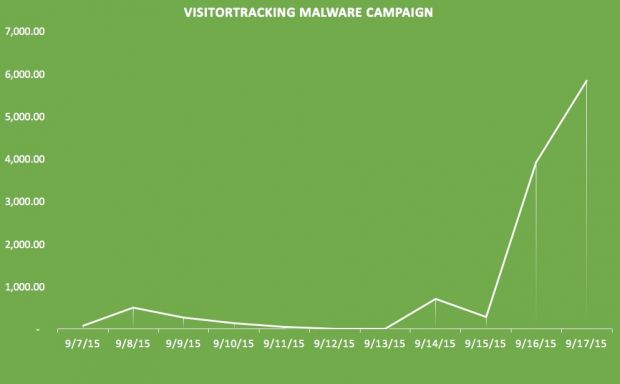
The campaign, which was named VisitorTracker after one of the JavaScript functions added to the .js files, usually calls to the vovagandon.tk domain, where the Nuclear Exploit Kit is hosted.
95% of all infected sites are using WordPress
Sucuri claims that 95% of the infected websites are running WordPress, and they suspect the initial infection took place with hackers exploiting vulnerable WP plugins.
The campaign had been first observed two weeks ago and has increased in intensity over the past few days.
According to Sucuri, out of all the compromised websites, 17% have already been blacklisted by Google and other popular blacklisting services.
Investigation steps & protection measures
To protect themselves and avoid being added to a Web blacklist, webmasters have a few tools at their disposal.
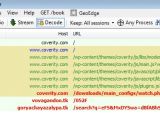
For starters, they can check their site's files for the malicious code by running the following command from their Linux terminal (if they use a Linux machine to host the site):
If your site is infected, you should remove the malicious code from the JS files, and update all plugins (and the WP core) immediately.

 14 DAY TRIAL //
14 DAY TRIAL //